
Web safety is key for new firms. Close to half of all web attacks hit small firms, and 60% of them close within six months. With the cost of lost data over $4 million, new firms must find cheap ways to stay safe and keep a good name.
Here is a short list of 30 free tools every new firm should think about to keep their systems safe, handle rules, and cut risks. These tools help with things like password safety, scanning for weak spots, safe talks, and checking networks:
- Password Safety: Bitwarden, KeePass
- Scanning for Weak Spots: OpenVAS, Trivy, Nikto
- Checking Networks: Zeek, Wireshark
- Safe Talks: Signal, Gpg4win
- Spotting Break-ins: OSSEC, Wazuh
- Testing Web Apps: OWASP ZAP, Burp Suite Community Edition
- Locking Data: VeraCrypt, Gpg4win
- Checking for Bad Software: Cuckoo Sandbox
- Help with Rules: Wazuh, Security Onion
Quick Tip: Begin with simple tools like Bitwarden, Signal, and Wireshark to meet quick safety needs. Slowly add more tough tools like Wazuh or OpenVAS as your firm grows.
Below is a full guide to these tools, how they help, and how they fit into your firm's web safety plan.
Why You Shouldn't Pay For Cybersecurity Tools - 9 Open Source Options for Small Companies
How to Pick Free Security Tools for Startups
When you consider that 43% of cyberattacks target small businesses and 60% of those impacted shut down within six months, selecting the right security tools becomes a matter of survival. For startups, free security tools can be a great starting point, but they must be chosen carefully to secure current operations and support future growth.
Here’s how to evaluate free security tools effectively.
Start with Compliance Requirements
The compliance standards you need to meet depend on your industry and customers. Common frameworks like SOC 2, HIPAA, ISO 27001, and GDPR each have specific security requirements.
"The cost of non-compliance is great. If you think compliance is expensive, try non-compliance." – Former U.S. Deputy Attorney General Paul McNulty
The good news? Many compliance frameworks overlap, so you can address multiple requirements with the same tools. Focus on free tools that support multiple frameworks instead of those tailored to just one.
Evaluate Integration Capabilities
Your security tools need to work together without creating gaps. Poor integration can lead to inefficiencies and vulnerabilities, increasing your team’s workload.
Look for tools that support key security mechanisms like authentication and access control, encryption, and vulnerability management. A well-integrated system ensures that all components can detect, prevent, and respond to threats effectively.
Streamlined integration can also reduce costs and save time. Once you’ve identified tools that integrate well, assess the community support behind them.
Assess Community Health and Support
Active communities are essential, especially for open-source tools, which make up many of the best free security solutions. Regular updates, active forums, and responsive maintainers are signs of a healthy community.
"Open source tools provide the flexibility, transparency, and feature updates driven by communities that are crucial in maintaining a good cybersecurity posture, especially in the development phase of your company." – Christina Todorova, Author, RoguePoint Security
Avoid outdated tools, as they can lead to compatibility issues and increased maintenance demands.
Consider Scalability and Growth Potential
What works for a small team may not be enough as your startup grows. Choose tools that can handle increasing data, users, and complexity without needing a complete overhaul.
Security measures should evolve with your company’s growth. Start with basic policies and gradually adopt more comprehensive controls as your team and operations expand.
Focus on Ease of Use and Automation
For startups with limited resources, simplicity and automation are key. Look for tools that are easy to configure and offer automation for tasks like updates, monitoring, and backups.
Some essential features to prioritize include:
- Password management and multi-factor authentication
- Automated software updates
- Continuous monitoring for unusual activities
- Automated backup systems
Evaluate Total Cost of Ownership
Even free tools come with hidden costs like implementation, training, and maintenance. Some free tools also have limitations that may push you toward paid versions as you scale.
With the average cost of a data breach for small businesses ranging from $120,000 to $1.24 million, investing time in evaluating tools now can save significant costs down the road.
Test Before Committing
Before selecting tools, conduct a security assessment to identify your critical assets and vulnerabilities. Use this information to narrow down the types of tools you need.
Set up pilot implementations with a few options to evaluate their performance. Pay attention to how well they integrate with your systems, the maintenance they require, and whether your team can use them effectively. Testing ensures the tools meet your compliance, integration, and automation needs.
For startups juggling multiple tools and compliance requirements, services like Cycore's GRC Tool Administration can simplify the process. These services help configure and maintain free tools to align with frameworks like SOC 2, HIPAA, and ISO 27001, ensuring your startup stays secure and compliant.
1. Zeek
Zeek is an open-source platform designed for network security monitoring. It works by analyzing network traffic in real time to detect threats and suspicious activities. Unlike firewalls or intrusion prevention systems, Zeek operates passively - capturing and analyzing data without interfering with network traffic.
Zeek’s capabilities are impressive. It generates over 70 logs, tracks more than 3,000 network events, and comes equipped with pre-built parsers for protocols like HTTP, SSL, DNS, and FTP. These features provide detailed, high-quality data that can be seamlessly integrated into SIEM platforms. With over 10,000 deployments worldwide and 6,400+ GitHub stars, Zeek has earned its reputation as a reliable tool.
"Zeek has been a cornerstone of the open-source and cybersecurity communities for decades."
When it comes to threat hunting, Zeek shines by monitoring traffic flows and identifying anomalies or malicious behavior. It profiles protocols and establishes baselines, allowing it to detect threats that traditional signature-based tools might miss.
"Zeek is a great source of network data for hunting, monitoring and analysis. If configured correctly, it does not boggle down the network or overload security teams with useless data." – Mark Viglione, Cybersecurity Engineer & Founder of Enigma Networkz
Zeek’s flexibility makes it easy to deploy. It can run on a variety of sensors - whether hardware, software, virtual, or cloud-based - and its logs integrate smoothly with platforms like Splunk and Elastic.
Beyond threat detection, Zeek’s detailed logging supports compliance with standards such as SOC 2, HIPAA, and ISO 27001. With over 20 years of federally funded research behind it and a community that has contributed 260+ packages, Zeek delivers enterprise-level monitoring without the hefty price tag.
For startups with limited resources, Zeek’s combination of advanced features and zero cost makes it an invaluable tool for building a strong network security foundation.
2. Security Onion
Security Onion stands out from standalone tools like Zeek by combining several open-source security tools into a single, all-in-one platform. It offers network monitoring, intrusion detection, and log management - all without any licensing costs.
"Security Onion is like a virtual watchdog for your computer network. It's a free and open-source software package that helps monitor suspicious activity on your network." – Pius Emmanuel Papka
Its user-friendly interface simplifies operations, making it a great option for small security teams managing limited resources.
The platform offers three deployment types to suit various needs. If you're testing or using a home lab, the evaluation setup is a good starting point. For small to medium-sized businesses, standalone deployments combine manager and sensor components on one machine, streamlining operations. For startups anticipating growth, distributed deployments separate backend and sensor components, making it easier to handle higher network traffic. This flexibility ensures that as your network scales, Security Onion can keep up.
For example, a recent home lab deployment showed that a standalone Security Onion setup could effectively capture full packet data and flag unusual outbound connections caused by a misconfigured application.
To run Security Onion, you'll need at least 12GB of RAM, 2–4 CPU cores, and around 200GB of storage. While virtual machines are an option, dedicated hardware generally performs better, especially for busy networks.
Setting up Security Onion requires some technical know-how but delivers extensive network visibility. You'll need to configure a dedicated management network interface with a static IP address. For better data quality, it's recommended to use dedicated TAPs instead of SPAN ports. The platform captures full packets and processes them through multiple detection engines simultaneously, offering a thorough monitoring solution.
To enhance performance, consider disabling unnecessary services like Snorby, prads, and http_agent. Security Onion also integrates seamlessly with existing infrastructures and provides detailed logs to help meet compliance requirements.
What makes Security Onion particularly appealing is its ability to deliver enterprise-grade network security monitoring capabilities - features that would typically cost thousands of dollars per month - in a free, open-source package that grows with your startup's needs.
3. Nmap
Nmap (Network Mapper) is often referred to as the "Swiss Army Knife" of networking for good reason - it’s a free, open-source tool that offers startups a powerful way to discover networks and audit security.
At its core, Nmap serves two main purposes: it maps out your network’s devices and services while also identifying vulnerabilities that could be exploited by attackers. By sending raw IP packets, Nmap uncovers available hosts, running services, operating systems, and even firewall settings. This gives you a detailed view of your network’s infrastructure. To show how simple it is to use, here are some basic commands to get started.
Nmap has received widespread recognition in the industry, including being named "Security Product of the Year".
For a basic port scan, you can use: nmap <target-IP>. This reveals open ports on the target device. If you want a deeper dive, scanning all 65,535 ports, use: nmap -p- <target-IP>. Adding the -sV flag enables service and version detection, helping you identify the specific applications running on those open ports.
Nmap's Scripting Engine (NSE) takes things a step further by automating vulnerability detection. For instance, running nmap --script vuln <target-IP> executes scripts to check for known vulnerabilities. You can also focus on specific services, like scanning for SMB vulnerabilities (including EternalBlue), with a command such as: nmap --script smb-vuln* -p445 <target-IP>.
For startups, Nmap has plenty of practical uses. It’s great for building network inventories, keeping tabs on service uptime, and planning upgrade schedules. Routine scans can uncover unauthorized devices, unnecessary services, or configuration changes that might pose security risks.
Nmap works across all major operating systems and comes with additional tools like Zenmap (a graphical user interface), Ncat (for data transfer and debugging), and Nping (for packet analysis). Its ability to output results in various formats - plain text, XML, or greppable - makes it easy to integrate with your existing security processes.
To balance speed and stealth, Nmap offers timing controls (ranging from T0 to T5). The SYN scan option, triggered with the -sS flag, is particularly useful for penetration testing.
To maximize its effectiveness, tailor your scans to specific goals, automate regular security checks, and use the results to prioritize system updates. For example, closing unnecessary ports with firewall rules can significantly enhance security. A command like iptables -A INPUT -p tcp --dport 23 -j DROP blocks Telnet access, which is often a security risk. When combined with monitoring tools like fail2ban or Suricata, Nmap becomes an essential part of a scalable, reliable security strategy.
4. Nikto

Nikto is an open-source web server scanner that helps startups uncover security vulnerabilities without spending a dime. Security expert Andrey Pautov describes it as:
"Nikto is a powerful, open‐source web server scanner designed to identify potential security vulnerabilities and configuration issues in web servers".
This tool stands out with its ability to detect over 6,700 vulnerabilities, check for outdated versions across more than 1,250 servers, and identify version-specific issues on over 270 server types. By focusing on web servers and HTTP-related issues, Nikto performs both passive and active scans to find dangerous files, outdated software, and misconfigurations that could leave your startup exposed to attacks. It's a cost-effective way to strengthen your security posture.
To run a basic scan, use the following command:
nikto -h <URL or IP address>
Nikto is compatible with Linux, macOS, and Windows. On Ubuntu/Debian systems, you can install it via your package manager, while macOS users can turn to Homebrew for installation.
Chris Gates, a respected security professional, highlights its importance:
"A must-have in any security toolkit, extensive database of known vulnerabilities and misconfigurations".
Nikto delivers quick results, emphasizing immediate detection of vulnerabilities. Its database is frequently updated through community contributions. To check your version and update it, run:
nikto.pl -Version
For startups looking to bolster security workflows, integrating Nikto into CI/CD pipelines is a smart move. This ensures vulnerabilities are caught early, before they make it to production. The tool supports multiple output formats - HTML, XML, CSV, and JSON - making it easy to share findings with stakeholders or link results to other security tools.
While Nikto excels at identifying vulnerabilities, it does not exploit them. This means you'll need to manually verify its findings and address any false positives. Pairing Nikto with tools like OWASP ZAP or Burp Suite Community Edition creates a well-rounded approach to web application security testing.
Automating scans with Nikto allows for continuous monitoring, keeping your defenses proactive. Up next, learn about Bitwarden for managing passwords securely.
5. Bitwarden
Bitwarden is an open-source password manager designed to provide startups with enterprise-level security without breaking the bank. Considering that 43% of small and medium businesses have been targeted by cyberattacks, this tool tackles a major risk - poor password practices.
The free version of Bitwarden is packed with essential features, making it a great option for startups. It allows you to securely store logins, notes, payment cards, and personal identities across all your devices. Plus, its built-in password generator ensures every account is protected with strong, unique passwords, all encrypted using AES 256-bit technology.
If you need to share credentials, Bitwarden’s free organization feature lets you add one additional user and create up to two collections. This is perfect for sharing critical information like social media logins, domain registrations, or cloud service credentials.
TechRepublic writer Jack Wallen praised Bitwarden, saying:
"My pick for best password manager easily belongs to Bitwarden - not only because it's open-source, but because it offers a perfect blend of simplicity and advanced features."
In fact, TechRepublic named Bitwarden the "Best Password Manager for SMBs" in July 2022.
To implement Bitwarden effectively, it's crucial to get leadership buy-in and announce the rollout across the company. Start by placing the most frequently used passwords into Bitwarden, encouraging employees to move away from less secure browser-based password managers. This small shift can make a big difference - while an 8-character password can be cracked in just 39 minutes, a 16-character password provides exponentially greater protection.
With the average cost of a data breach expected to hit $4.88 million in 2024 - a 10% increase from the previous year - investing in proper password management isn’t just about security; it’s a smart financial decision. Bitwarden also meets key compliance standards like GDPR, SOC 2, HIPAA, Data Privacy Framework (DPF), and CCPA.
When it’s time to expand, Bitwarden's paid plans are budget-friendly, starting at $4 per user per month for Teams (billed annually). The free tier provides a strong starting point, ensuring your startup is equipped with secure password practices that can scale as you grow.
Next, discover how Signal keeps team communications private with end-to-end encryption.
6. Signal
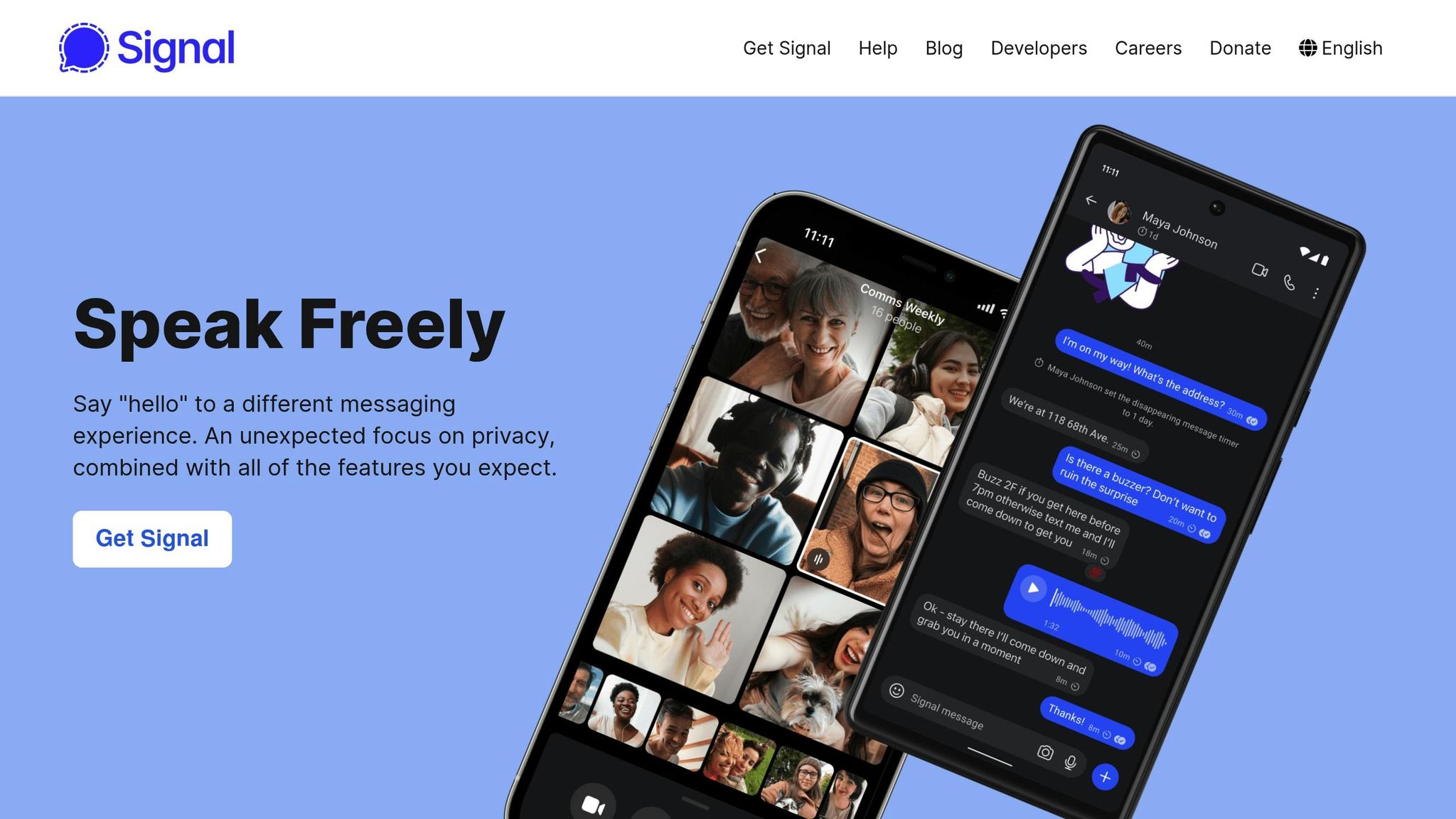
Signal is a free, open-source messaging app designed to provide top-notch end-to-end encryption, making it a go-to choice for startups seeking secure communication. With around 70 million active users and over 220 million downloads worldwide, Signal has built a reputation as a reliable and secure messaging platform.
What sets Signal apart is its robust encryption. As explained on Signal.org:
"State-of-the-end-to-end encryption (powered by the open source Signal Protocol) keeps your conversations secure. We can't read your messages or listen to your calls, and no one else can either. Privacy isn't an optional mode - it's just the way that Signal works. Every message, every call, every time."
Signal's encryption framework uses advanced techniques, including the Double Ratchet Algorithm, prekeys, and a triple Elliptic-curve Diffie-Hellman handshake. It relies on cryptographic tools like Curve25519, AES-256, and HMAC-SHA256 to ensure that only the sender and receiver can access messages - Signal itself cannot decrypt them.
For startups, Signal offers several tools tailored for secure collaboration. It supports large group chats of up to 1,000 participants, enabling teams to share photos, GIFs, and files - all protected by strong encryption. This makes it a great fit for fast-paced, collaborative environments. Additionally, users can set disappearing messages to automatically delete after a specific time, reducing the risk of sensitive information lingering unnecessarily.
Signal’s dedication to privacy is evident in its minimal data retention practices. The app only stores your phone number, encryption keys, and basic profile details. As a non-profit, Signal operates without ads or trackers, further emphasizing its focus on user privacy. It also works across multiple platforms, including Windows, macOS, Linux, iOS, and Android, ensuring flexibility for diverse teams.
To make the most of Signal’s security features, consider enabling options like Screen Security, which blocks message previews in your device’s app switcher, and Registration Lock, which helps prevent unauthorized access to your account. Setting disappearing messages as the default for all new chats can also safeguard sensitive discussions.
One creative example of Signal’s application comes from an online marketplace that integrated Signal with Bubble.io to create a secure, real-time chat feature for deal negotiations.
Best of all, Signal is completely free - no subscription fees, no ads - making it an excellent choice for startups on tight budgets.
Next, we’ll explore OSSEC, a powerful tool for host-based intrusion detection that keeps your systems secure 24/7.
7. OSSEC
OSSEC is an open-source, host-based intrusion detection system (HIDS) designed to keep a close watch on your servers and workstations. With more than 500,000 downloads every year, it's a trusted choice for enterprises, small businesses, and government agencies around the world.
As the official documentation puts it:
"OSSEC is a platform to monitor and control your systems. It integrates HIDS, log monitoring, and SIM/SIEM into one powerful open-source solution."
What sets OSSEC apart is its ability to provide deep, system-level monitoring. Unlike network-based solutions that focus on traffic between systems, OSSEC digs into file changes, log analysis, and even hunts for hidden rootkits.
How OSSEC Works
OSSEC uses a centralized client-server setup. Lightweight agents installed on monitored systems send data back to a central manager, which processes security events and generates alerts.
One of its standout features is file integrity monitoring, which keeps a constant eye on critical system files. If any unexpected changes occur, administrators are alerted immediately - this is crucial for spotting unauthorized modifications that could signal a breach.
On top of that, OSSEC analyzes logs from a wide range of sources, including operating systems, firewalls, and web servers. This helps identify suspicious patterns, such as repeated failed login attempts or unusual user activity. It also scans for rootkits - malicious tools that hide their tracks by altering files, processes, or kernel modules.
Real-Time Alerting and Active Response
OSSEC ensures that security incidents are brought to your attention right away. Alerts can be sent via email, syslog, or integrated with tools like Splunk or Elasticsearch. Its Active Response feature takes things a step further by automatically blocking IP addresses after repeated failed logins or disabling compromised accounts.
Compliance Support
For startups navigating regulatory requirements like PCI DSS or HIPAA, OSSEC offers helpful features such as file integrity monitoring, log inspection, and policy enforcement. It even automates audit trails, capturing details like user IDs and timestamps to assist with over 100 PCI controls.
Best of all, OSSEC is free and works across multiple operating systems, making it an excellent choice for startups looking to bolster their security without breaking the bank.
Next, let's dive into Suricata to strengthen your network-level monitoring.
8. Suricata

Suricata is an open-source, high-performance network threat detection engine that serves as an Intrusion Detection System (IDS), Intrusion Prevention System (IPS), and Network Security Monitoring (NSM) tool. Widely trusted by major vendors, it integrates effortlessly into various security setups.
For startups, Suricata stands out thanks to its ability to analyze network traffic at impressive speeds while identifying threats like malware, phishing attempts, and unauthorized access. Its multi-threaded design ensures faster detection, making it a great fit for businesses scaling their operations.
How Suricata Protects Your Network
Suricata works by inspecting network packets in real-time, using signature-based detection and deep packet inspection to identify threats. It automatically detects and processes multiple protocols at high speeds, including HTTP, TLS, DNS, FTP, and SMB.
The tool is flexible in deployment. You can start in IDS mode to monitor suspicious activity without interfering with traffic or switch to IPS mode to block malicious activity as it happens.
Seamless Integration and Compatibility
One of Suricata's strengths is its compatibility with Snort rules, giving you access to a vast library of pre-existing detection rules. It also generates detailed logs in JSON format, which makes integration with SIEM tools and the Elastic Stack (Elasticsearch, Kibana, Beats, and Logstash) simple. This streamlined logging process supports compliance efforts and enhances threat response, complementing the security measures established by other monitoring tools.
Getting Started with Suricata
Begin with IDS mode to observe network activity and fine-tune detection rules. Tailor these rules to match your specific network setup and make regular updates to stay ahead of new threats.
Suricata's active development community continuously improves the platform, ensuring it remains effective against increasingly sophisticated threats.
Next, consider exploring MISP, a threat intelligence platform that pairs well with Suricata’s monitoring capabilities.
9. MISP
MISP, short for Malware Information Sharing Platform, is an open-source tool designed to help organizations share, store, and analyze indicators of compromise (IOCs). It's a go-to solution for over 6,000 organizations across multiple industries, offering a collaborative way to strengthen cybersecurity efforts.
The platform organizes both technical and non-technical malware data in a structured format. It also automatically connects the dots between threat attributes, making it easier to integrate with tools for detection, forensics, and intrusion prevention.
Building a Threat Intelligence Network
One of MISP's standout features is its focus on collaboration. Startups can either join existing MISP communities or create their own to share threat intelligence. This is particularly helpful for startups with limited resources to conduct in-depth threat research. MISP supports a broad range of threat data, including malware samples, attack patterns, vulnerabilities, and IOCs. Its built-in correlation engine helps detect patterns and trends, enabling teams to identify potential threats before they turn into bigger problems.
Integration and Automation Made Simple
MISP is built to work seamlessly with existing security setups. Through its RESTful API and Python module (PyMISP), startups can automate the sharing of IOCs with firewalls, endpoint agents, and intrusion detection systems. Its structured data format and flexible distribution models make secure information sharing straightforward and efficient.
How to Get Started with MISP
To start using MISP, startups can either request access to existing MISP communities relevant to their industry or deploy their own instance for internal use. Begin by organizing IOCs within MISP and gradually expand intelligence sharing with trusted partners. The platform also supports widely recognized threat intelligence frameworks like MITRE ATT&CK and uses standardized formats such as STIX, ensuring compatibility with industry standards. Providing your team with MISP training can further enhance its effectiveness.
With a solid foundation in MISP, you’ll be ready to explore OpenCTI, a platform that complements MISP by offering advanced analysis tools to deepen your threat intelligence capabilities.
10. OpenCTI
OpenCTI (Open Cyber Threat Intelligence) is an open-source platform designed to help startups manage and visualize threat intelligence effectively. It’s particularly appealing to startups because it addresses compliance needs while keeping costs in check. OpenCTI provides enterprise-level features through its free Community Edition, available on GitHub.
The platform organizes threat data using the STIX2 standard format, ensuring compatibility with widely used industry frameworks. This makes it easier to share threat intelligence with partners, vendors, and security communities. With this structure, teams can transform raw threat data into meaningful insights.
Turning Raw Data into Insights
OpenCTI centralizes threat information from various sources into a single, unified knowledge graph. By connecting tactics, techniques, procedures, observables, reports, and victim profiles, it provides a detailed view of the threat landscape. Its graph-based visualization tools make it simple for teams to uncover connections, recognize patterns, and detect emerging attack trends.
Real-World Benefits for Security Teams
Organizations using OpenCTI have reported significant improvements in their security operations. For example, Sopra Steria integrated OpenCTI with Microsoft Sentinel, which helped them link scattered alerts into actionable patterns and cut down false positives by more than 50%.
Similarly, Intrinsec achieved a 65% reduction in investigation times, grew their threat knowledge base to over 3 million entries, and reduced feed redundancy by 25%.
Seamless Integration with Security Tools
OpenCTI is built to complement existing security setups. It offers over 300 connectors and supports RESTful APIs, GraphQL, and Live Streams for smooth integration with SIEM systems, firewalls, and endpoint detection tools.
"By bringing IBM X-Force intelligence into OpenCTI, we're enabling security teams to work more efficiently with some of the industry's most valuable threat data. The combination of elite intelligence and powerful visualization creates a compelling solution for organizations seeking to strengthen their security posture."
- Jan Johansen, SVP Global Alliances at Filigran
How to Get Started with OpenCTI
Getting started with OpenCTI is straightforward. You can deploy it using Docker, manual installation, or cloud-based solutions like Terraform and Helm charts. Once set up, connect your existing threat feeds through OpenCTI’s extensive library of connectors. Features like confidence level assessment and temporal tracking help prioritize threats based on their reliability and relevance. Additionally, the platform's indicator lifecycle management automatically removes outdated threats, helping reduce alert fatigue.
11. OWASP ZAP

OWASP ZAP (Zed Attack Proxy) is a free, open-source web application security scanner that has been helping developers secure their applications since 2010. Designed to cater to both beginners and seasoned security professionals, ZAP is an excellent choice for startups looking to identify vulnerabilities during development and testing without stretching their budget.
What sets ZAP apart is its ability to perform both automated and manual security testing. Acting as a "man-in-the-middle proxy", it intercepts and examines messages exchanged between browsers and web applications, offering teams valuable insights into potential security flaws.
Why ZAP Stands Out for Startups
ZAP comes packed with features tailored to modern web application security needs. These include:
- Proxy-based scanning
- Automated and manual penetration testing tools
- Active and passive scanning
- Add-on extensibility
- Spidering and API testing
- CI/CD integration
- Report generation
The tool is adept at identifying common vulnerabilities such as SQL injection, cross-site scripting (XSS), CSRF, broken authentication, and insecure direct object references. With 60% of web applications vulnerable to XSS attacks and 91% of organizations facing API-related issues in 2021, tools like ZAP are critical for ensuring robust security.
A Success Story: FinSecure
FinSecure, a fintech startup, integrated ZAP into its CI/CD pipeline using Jenkins to maintain continuous security validation for its web application. By doing so, the company achieved:
- Early detection and resolution of vulnerabilities
- Automated security testing
- Lower costs compared to manual testing
- Improved collaboration between development and security teams
This case demonstrates how ZAP can effectively streamline security practices without compromising efficiency.
How to Get Started with ZAP
ZAP offers flexibility in how it runs - it can be used via the command line, as a desktop application, or as a daemon. Its Automation Framework, controlled through a single YAML file, simplifies the process.
To make the most of ZAP:
- Start with manual exploration to map out your application's structure.
- Define contexts and run automated scans using both traditional and AJAX spiders.
- Integrate ZAP into your CI/CD pipeline for continuous security testing throughout the development lifecycle.
ZAP also supports various reporting formats, including HTML, XML, and JSON, making it easy to share findings with your team or stakeholders.
Things to Keep in Mind
While ZAP is a powerful tool, it’s not without its challenges. It can produce false positives that require manual verification, and active scanning might temporarily affect application performance. Additionally, detecting vulnerabilities tied to complex business logic often requires manual testing, and setting up advanced features can be tricky.
Despite these limitations, ZAP's affordability and user-friendly interface make it a go-to solution for startups serious about securing their web applications.
Up next, we’ll dive into another tool that strengthens your cybersecurity defenses.
12. Snort

Snort is a free, open-source intrusion detection and prevention system (IDS/IPS) and is one of the most widely used tools for network security monitoring. With over 5 million downloads and a community of more than 600,000 registered users, Snort offers startups a reliable way to safeguard their networks.
What sets Snort apart is its ability to monitor network traffic in real time, logging packets and identifying suspicious activity as it happens. It uses a rule-based system to detect malicious behavior, combining techniques like anomaly detection, protocol analysis, and signature inspection.
How You Can Use Snort
Snort's versatility means it can be deployed in different ways depending on what your startup needs:
- Packet sniffer: Monitors and analyzes network traffic in real time.
- Packet logger: Records network activity for future analysis.
- Intrusion prevention system: Actively blocks threats before they can cause harm.
Snort is particularly effective at detecting various types of attacks, including denial-of-service (DoS), distributed DoS (DDoS), CGI attacks, buffer overflows, and port scans. When used as an inline system, it can block malicious packets before they reach their destination.
Getting Snort Up and Running
To configure Snort, you’ll work with its snort.conf file, which defines how it analyzes network traffic and handles potential threats. Key setup steps include defining network variables like HOME_NET for internal traffic and EXTERNAL_NET for external traffic.
For added protection, you can create custom rules to block specific attack patterns. Snort provides two primary rule sets: the free Community Ruleset and the Snort Subscriber Ruleset, which is maintained by Cisco Talos. This flexibility allows you to tailor Snort to your startup’s unique security needs.
Tips for Optimizing Snort
To make Snort run efficiently without overloading your system, consider these steps:
- Disable unnecessary rules to keep things streamlined.
- Adjust thresholds to cut down on false positives.
- Enable fast pattern matching for quicker detection.
- Turn off preprocessor features you don’t need to reduce resource usage.
Keep Snort and its rules updated regularly, fine-tune configurations, and test its performance to ensure it meets your needs. You might also want to integrate Snort with other security tools or SIEM systems for a more comprehensive monitoring setup.
Snort’s architecture includes components like a packet decoder, detection engine, logging and alerting system, and preprocessors. It’s compatible with multiple operating systems, including Linux and Windows, making it a flexible option for startups. Up next, explore another essential tool to enhance your penetration testing toolkit.
13. Metasploit Framework
When it comes to strengthening network and system defenses, Metasploit offers startups a powerful way to simulate real-world cyberattacks. This open-source penetration testing platform allows businesses to uncover vulnerabilities in their systems by mimicking the tactics of malicious actors. Essentially, it provides a controlled environment where you can test your defenses and identify weak points before someone else does.
What sets Metasploit apart is its extensive library of 2,074 exploits and 592 payloads. This robust toolkit enables startups to evaluate their security posture by running realistic attack scenarios. Understanding how Metasploit works can help you proactively address potential risks.
How Metasploit Works for Startups
Metasploit has two key components: the Framework and the Console. The Framework is a collection of tools and libraries designed for creating and testing exploit code, while the Console provides an intuitive interface to access these capabilities. You can download Metasploit directly from Rapid7 or use the version included with Kali Linux.
The testing workflow involves configuring an exploit module, pairing it with a payload, targeting your system, and launching the test. This process closely mirrors the steps an attacker might take, giving you a clear picture of potential vulnerabilities and data risks.
Key Features That Matter for Startups
Metasploit’s modular design makes it incredibly flexible, catering to a wide variety of platforms and applications. It supports over 25 platforms - including Android, PHP, Python, Java, and Cisco systems - allowing startups to assess vulnerabilities across diverse environments.
Metasploit also integrates seamlessly with reconnaissance tools like Nmap and Nessus, making it easier to identify and prioritize vulnerabilities. Its post-exploitation tools, such as privilege escalation, packet sniffing, keylogging, and persistent backdoor creation, help you understand the potential aftermath of a breach.
Here’s a quick breakdown of its standout capabilities:
| Feature Category | Capabilities |
|---|---|
| Exploit Development | Launch exploits on vulnerable systems, create custom exploits, and use an updated exploit database |
| Payload Options | Includes Meterpreter, Shellcode, and Staged Payloads |
| Post-Exploitation | Extract credentials, elevate privileges, capture keystrokes, and take screenshots |
| Auxiliary Modules | Perform scanning, password cracking, service enumeration, and more |
Getting Started Safely
Given its popularity among ethical hackers and cybercriminals alike, it’s essential for startups to approach Metasploit with caution and responsibility. Familiarizing yourself with its tools and features can significantly improve your ability to defend against similar attack methods.
Always use Metasploit in a dedicated test environment, such as virtual machines, to ensure safety. Make sure you only test systems you own or have explicit permission to test. Keeping your Metasploit installation up to date ensures access to the latest exploit signatures and tools.
The MSFconsole serves as the primary hub for Metasploit, offering centralized access to all its features. Beginners might find the Armitage GUI helpful for visualizing targets, while resource scripts can automate more complex testing workflows. Additionally, auxiliary modules simplify vulnerability scanning, while advanced payloads like Meterpreter provide insights into what attackers could achieve, such as process migration or screenshot capture.
14. Cuckoo Sandbox
When suspicious files or URLs find their way into your startup’s environment, you need a secure way to analyze them without jeopardizing your systems. That’s where Cuckoo Sandbox steps in. This free, open-source tool automates malware analysis by executing potentially dangerous files in completely isolated environments. It ensures harmful files are contained and examined safely.
Cuckoo’s capabilities are particularly helpful for startups. It doesn’t just identify malicious files - it provides detailed insights into API calls, file modifications, network traffic, memory dumps, and even screenshots captured during execution. This automated process supports faster incident response and strengthens your overall threat detection efforts.
How Cuckoo Works for Startup Security
Cuckoo operates on a Linux host system with nested Windows guests for analysis. When you submit a suspicious file, the system executes it in an isolated environment, monitoring its every move. It supports a wide range of file types, including Windows executables, PDFs, Microsoft Office documents, URLs, PHP scripts, ZIP files, Java JAR files, and Python files. Throughout the process, Cuckoo records network activity, tracks system changes, and compiles detailed reports of Indicators of Compromise (IOCs), helping your team respond to threats quickly.
Key Features That Benefit Startups
Cuckoo’s modular design makes it adaptable to your specific security needs. It can process multiple suspicious files simultaneously, which is particularly useful when dealing with bulk email attachments or file uploads. The system also offers both command-line and web-based interfaces. The web interface simplifies operations by providing usage statistics, file submission options, and quick access to recent analysis reports.
Here’s a breakdown of some of Cuckoo’s core analysis capabilities:
| Analysis Component | Details Captured |
|---|---|
| API Monitoring | Logs all API calls made by malware processes |
| File Activity | Tracks files created, deleted, or downloaded during execution |
| Network Traffic | Provides a full network trace in PCAP format |
| Visual Evidence | Captures desktop screenshots during malware execution |
| Memory Analysis | Generates full memory dumps of affected processes |
Setting Up Cuckoo Safely
To deploy Cuckoo in your startup’s environment, you’ll need a Linux host machine equipped with VirtualBox 5.2 and Python 2.7. It’s recommended to use Windows 7 as the guest operating system for analysis, with the network adapter set to "Host Only Adapter" to maintain strict isolation.
For instance, the security firm Bridewell successfully configured Cuckoo on an Ubuntu desktop to analyze WannaCry ransomware. Their approach shows that even startups can use Cuckoo to safely investigate advanced threats.
Practical Tips for Startup Implementation
When implementing Cuckoo, you might want to route traffic through TOR to conceal your sandbox’s source IP address. Alternatively, you can disable network connectivity entirely during analysis for added security. Integrating the IOCs generated by Cuckoo into your Security Operations Center (SOC) can further enhance your defenses. These steps ensure Cuckoo becomes a valuable part of your broader security framework.
15. Kali Linux
If your startup needs a reliable platform for security testing, Kali Linux is a go-to solution. This Debian-based Linux distribution comes packed with over 600 tools designed for penetration testing and security auditing, all developed and maintained by Offensive Security.
Unlike general-purpose operating systems, Kali Linux is purpose-built for security professionals, web administrators, and anyone conducting authorized security assessments. The best part? It’s free, allowing startups to perform thorough security evaluations without adding to their budget.
Why Startups Turn to Kali Linux
Kali Linux saves you from the headache of manually installing and configuring security tools. Instead of spending weeks setting up a testing environment, you get instant access to tools for tasks like network analysis, vulnerability scanning, password cracking, wireless security, and even digital forensics. For startups juggling limited resources and tight deadlines, this kind of efficiency is priceless.
The operating system uses a rolling release model, meaning it’s regularly updated with the latest tools and features. That way, your team always has access to cutting-edge security capabilities without needing to overhaul the system. Plus, Kali Linux supports a variety of platforms, including x86, ARM, and cloud environments, giving you flexibility in how and where you deploy it.
Key Features for Security Testing
Kali Linux acts as a centralized hub for penetration testing, equipping your team to uncover vulnerabilities before bad actors do. With specialized tools for nearly every aspect of security assessment, it helps your startup strengthen its defenses systematically.
Safe Deployment for Startups
For startups, the safest way to use Kali Linux is by running it on a virtual machine. This approach isolates it from your production systems while still offering full functionality. To get started, install Kali Linux using the official ISO, then update it immediately with the command:
sudo apt update && sudo apt full-upgrade -y
This ensures you have the latest patches and tools.
This setup process, combined with its extensive toolkit, makes Kali Linux an essential resource for any startup looking to prioritize security.
Best Practices for Implementation
Using Kali Linux effectively means following strict security and legal guidelines. Always ensure you have explicit permission to test the systems you're assessing. Stick to using virtual machines or sandboxed environments to keep your Kali Linux installation isolated from production networks. Additionally, safeguard your setup with strong access controls, full-disk encryption, and robust authentication.
To keep your tools current, update regularly and consider adding more utilities with commands like:
sudo apt install kali-tools-top10
This installs the most commonly used security testing tools, giving you even more flexibility to tailor the system to your needs.
Kali Linux isn’t just a tool - it’s also a learning platform. It features prominently in professional certifications like Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP), making it a great way for your team to build their skills while securing your systems.
16. Wireshark
Wireshark offers a detailed, real-time view of network traffic, making it a crucial tool for troubleshooting and investigating network issues. As a free, open-source network protocol analyzer, it's widely recognized for its ability to simplify complex network data into actionable insights - an asset for startups looking to optimize their operations.
With over 20 million downloads each year and support in more than 20 languages, Wireshark has become a staple for IT professionals worldwide. Managed by the Wireshark Foundation, a non-profit organization, the platform benefits from an active community of over 100,000 contributors who continuously improve its features and functionality.
Why Startups Turn to Wireshark for Network Analysis
Wireshark is a key part of a well-rounded security toolkit, offering a level of network visibility that many other tools can't match. It transforms raw network data into clear, understandable information, helping teams uncover what's happening behind the scenes. Unlike simpler monitoring tools that only provide surface-level metrics, Wireshark dives deep, analyzing hundreds of protocols - from common ones like HTTP and DNS to more specialized enterprise-level protocols.
"Wireshark is your go-to tool for network analysis and debugging." - Wireshark.org
The tool is particularly effective at identifying issues like network bottlenecks, packet loss, and misconfigurations. For startups with small IT teams, this kind of insight is invaluable for diagnosing problems quickly and avoiding costly downtime.
Features That Make Wireshark Stand Out
One of Wireshark's standout features is its protocol dissectors, which decode and display network protocols in human-readable formats. This eliminates the need to interpret raw hexadecimal data or memorize complex protocol specifications, making it accessible even for less experienced team members.
The platform supports multiple network interfaces, including wireless, Ethernet, and virtual connections. Its real-time packet capturing capability allows you to monitor network activity as it happens. Additional features like powerful filtering options and color-coded displays make it easier to spot trends and anomalies, while export options let you customize the data for your specific needs.
How Startups Can Leverage Wireshark for Security
Mohnish Rathod, Deep Tech Consultant & India Sales Lead at Network Science, likens Wireshark to a detective for your network:
"Imagine Wireshark as a network detective. It lets you eavesdrop (with permission, of course!) on conversations happening across your network. This can be helpful in a few ways. It can help you with: Inspect traffic for malware or hacking. Find security weaknesses in your network. Investigate security breaches. Monitor traffic for performance issues."
Wireshark is particularly adept at identifying malicious traffic patterns, such as unauthorized data transfers or denial-of-service attacks. By analyzing packet details, your team can detect suspicious activity that could indicate a security breach in progress.
Mehregan Etemadi, Cloud Solution & Security Architect, highlights additional security benefits:
"Wireshark aids in network security by: Detecting attacks, such as unusual data packets or suspicious connections. Monitoring traffic to identify unencrypted sensitive data and address security gaps. Uncovering vulnerabilities in network configurations or protocols to enhance security policies. Conducting forensic investigations post-security incidents to understand attacks and take appropriate measures."
Tips for Using Wireshark Effectively in Startups
To get the most out of Wireshark, focus on capturing only the data you need. This reduces the volume of information to analyze and minimizes the risk of exposing sensitive data unnecessarily. Always ensure you have proper authorization before capturing network traffic, especially in environments where confidential information might be involved.
Keep the tool updated to take advantage of the latest protocol support and security patches. When storing capture files, secure them with restricted access, as they may contain sensitive network details.
Be aware of the potential performance impact when capturing traffic on busy networks. Using dedicated capture devices or applying filters can help minimize disruptions. Finally, remember that Wireshark is best used as an investigative tool. It excels when you need to dig deeper into issues flagged by other monitoring solutions or gain a detailed understanding of specific network behaviors.
sbb-itb-ec1727d
17. ClamAV
ClamAV stands out as one of the most reliable free antivirus options for startups, offering strong malware detection capabilities. This open-source antivirus toolkit is designed to identify trojans, viruses, and other harmful threats that could jeopardize your startup's operations and data security.
What makes ClamAV especially useful is its compatibility across Linux, Windows, and macOS, making it a flexible choice for startups working with diverse technology stacks. Its signature database, updated multiple times daily, allows it to detect millions of viruses, worms, and trojans, ensuring your systems remain protected.
Why Startups Choose ClamAV
For resource-conscious startups, ClamAV provides a budget-friendly solution that frees up funds for other critical needs. It supports a wide range of file formats and signature languages, offering thorough protection against a variety of threats.
Performance and Detection Accuracy
ClamAV has a proven track record in malware detection. In a 2011 test conducted by The Shadowserver Foundation, it successfully identified 75.45% of viruses in their sample set. Despite its effectiveness, it operates with relatively modest system requirements.
Deployment Options for Startups
ClamAV offers two main deployment modes: one-time scans for thorough audits and a service mode for real-time, on-demand protection.
For startups managing file uploads through web applications, ClamAV can be integrated to scan files before they are processed or stored. This ensures malicious files are blocked before they can compromise your systems, safeguarding both your infrastructure and customer data. These flexible deployment options make ClamAV a valuable addition to any security strategy.
Automating Updates and Integrations
Automating virus definition updates with ClamAV is straightforward. Using the freshclam utility, you can set up a cron job to update definitions every six hours:
0 */6 * * * /usr/bin/freshclam
. ClamAV also integrates seamlessly with mail servers, filtering out malicious attachments before they reach employee inboxes - a particularly useful feature for startups with smaller IT teams.
User Feedback and Support
ClamAV has earned a 4 out of 5-star rating on SoftwareSuggest, with users praising its email scanning features, frequent updates, and detailed documentation. The active user community provides a wealth of resources, including troubleshooting guides and integration tips, all available at no extra cost.
Managing System Resources
While ClamAV delivers strong protection, its scans can consume significant system resources. To optimize performance, monitor memory usage, set file size limits, and consider using TCP socket scanning for environments with high file volumes. Scheduling intensive scans during off-peak hours can also help reduce strain on your systems.
18. KeePass
KeePass is a free, open-source password manager that has been a trusted tool for secure, local password storage since 2003. It uses powerful encryption algorithms like AES-256, ChaCha20, or Twofish to protect your data. With over two decades of use and a spotless record of zero breaches, KeePass ensures your passwords stay safe on your device [74].
Why Security Experts Recommend KeePass
KeePass has undergone rigorous scrutiny, including an audit by the European Commission's Free and Open Source Software Auditing project, which found no security issues. It’s also endorsed by the German Federal Office for Information Security and approved for use by French public agencies. Renowned cryptography expert Bruce Schneier highlighted the importance of open-source security:
"As a cryptography and computer security expert, I have never understood the current fuss about the open source software movement. In the cryptography world, we consider open source necessary for good security; we have for decades. Public security is always more secure than proprietary security."
– Bruce Schneier
Key Features for Startup Teams
KeePass provides multiple ways to secure your password vault. You can rely on a master password, enhance it with a key file (e.g., stored on a USB drive), or use Windows user account integration. Additionally, its Auto-Type feature can automatically input credentials, minimizing clipboard-related risks. These features make KeePass an excellent choice for startups looking to establish strong security practices.
Tips for Secure KeePass Setup
When setting up your KeePass database, start with a strong master password. Aim for at least 12 characters, mixing uppercase and lowercase letters, numbers, and special characters. For added security, combine your master password with a key file. Always download KeePass directly from its official website (keepass.info) to avoid counterfeit versions.
Managing Teams and Backups
In collaborative environments, protecting shared credentials is just as vital as securing individual access. KeePass allows you to create separate databases for different user levels, ensuring secure team management. Its portable design also lets you run it from a USB drive. To prevent data loss, regularly back up your .kdbx and key files to external drives or secure cloud storage. Enabling auto-lock adds an extra layer of protection, keeping your credentials safe if left unattended .
19. CyberChef
CyberChef is a free, browser-based tool often referred to as a "cyber Swiss army knife." Created by the UK's GCHQ in 2017, it simplifies tasks like encryption, decoding, compression, and data manipulation - all without requiring any coding skills.
"A simple, intuitive web app for analysing and decoding data without having to deal with complex tools or programming languages. CyberChef encourages both technical and non-technical people to explore data formats, encryption and compression." – gchq.github.io
Privacy-Focused Data Processing
One standout feature of CyberChef is its commitment to privacy. All data processing happens locally within your browser, ensuring that sensitive information stays on your device. It can handle files up to around 2GB, depending on your browser's capabilities. This makes it especially useful for startups dealing with confidential data or those working under strict compliance rules.
Must-Have Features for Security Teams
CyberChef offers a wide range of operations, from straightforward encoding tasks to advanced cryptographic processes. Its "Magic" operation is particularly helpful, as it identifies encoding types and suggests the right actions automatically - perfect for team members who aren't deeply technical. You can also save and share "recipes" (custom workflows) to streamline analysis across your team and improve efficiency.
These features make CyberChef an excellent tool for real-world security investigations, helping teams tackle complex problems with ease.
Practical Security Use Cases
When it comes to investigating potential threats, CyberChef shines. For example, if you encounter a suspicious PowerShell command encoded in Base64, the tool allows you to extract the Base64 segment, decode it, and convert it from UTF-16LE to uncover the underlying command.
It’s also great for extracting indicators of compromise (IOCs) like IP addresses, URLs, and file hashes from unstructured text. Using its extraction operations, you can quickly pull out relevant data, sort it, and remove duplicates for further analysis. Additionally, converting timestamps into UTC with the "From UNIX Timestamp" operation is straightforward, making it easier to analyze logs and respond to threats efficiently.
Offline Deployment Options
For general use, the web version of CyberChef works well. However, if you're handling highly sensitive data, you can download the standalone version or deploy it via Docker. This ensures that your data analysis remains completely offline while retaining all the tool's features.
To help new users get up to speed, CyberChef includes built-in contextual help. Hover over any feature and press F1 for detailed guidance, enabling your team to master the tool quickly and confidently.
20. Trivy
Trivy is a standout tool for startups looking to bolster container security without breaking the budget. This free, open-source vulnerability scanner from Aqua Security checks container images, file systems, Git repositories, and Kubernetes clusters for vulnerabilities, misconfigurations, secrets, and even license risks.
"Trivy is a comprehensive security scanner. It is reliable, fast, extremely easy to use, and it works wherever you need it." - aquasecurity.github.io
Why Container Security Matters for Startups
For startups, container security isn't just an option - it's essential. Here's why: 54% of Docker Hub images contain sensitive information, and these images have been downloaded over 132 billion times. That’s a staggering risk. Trivy steps in to address this issue with lightweight, fast scanning that fits seamlessly into development workflows. It’s ready to use right away, delivering quick and actionable results.
What Makes Trivy Stand Out?
Trivy’s ability to scan multiple targets is a game-changer. It doesn’t just stop at container images - it also scans:
- Entire file systems for vulnerabilities
- Git repositories for exposed secrets
- Kubernetes clusters for misconfigurations
It uses multiple up-to-date vulnerability databases to ensure thorough coverage. Plus, it caches scan results, which speeds up future scans - a handy feature for teams running frequent checks.
Real-World Success
Trivy isn’t just theory - it’s proven in practice. For example, in December 2024, Jit started using Trivy to scan Dockerfiles and detect vulnerabilities in C# NuGet packages. They’ve since expanded its use to scan containers in registries and during runtime. Security experts have been vocal about its impact. Mustafa Akin from Resmo shared:
"I love how Trivy democratized dependency scanning to the masses as a free and extremely easy to use tool, with also a permissive license. This used to be a gated community with predatory security vendors charging premium, and they were not half as good as Trivy."
Seamless CI/CD Integration
For startups embracing DevOps, Trivy’s integration with CI/CD pipelines is a huge plus. You can configure it to automatically scan images during builds, set thresholds to fail builds with critical vulnerabilities, and generate detailed reports to track progress. This approach catches vulnerabilities early, allowing teams to fix issues before they escalate.
How to Get Started with Trivy
Kick things off by scanning your existing container images to establish a baseline for security. Use minimal base images and stick to trusted repositories like Docker Hub to limit your attack surface. Trivy’s filtering options let you focus on critical and high-severity vulnerabilities. Don’t forget to keep its vulnerability databases updated and train your team to interpret scan results effectively.
21. Lynis
Lynis is an open-source security auditing tool designed for Linux, macOS, and Unix systems. Since its debut in 2007, it has been a reliable choice for system-level security checks. For startups with limited IT budgets, Lynis offers robust security auditing without the financial strain of enterprise-level tools.
What sets Lynis apart is its non-intrusive nature. Unlike some tools that might interfere with your system, Lynis performs hundreds of security tests without altering your system during the process. This makes it an excellent fit for startups, as it integrates smoothly into your operations without disrupting daily workflows.
Why Startups Should Consider System-Level Security Auditing
Lynis goes beyond what external scanners can accomplish. By operating directly within your system, it uncovers configuration issues and missing patches that external tools might overlook.
Its modular design is another standout feature. Lynis adapts to your specific setup, whether you're running a straightforward Ubuntu server or a more intricate FreeBSD environment. It customizes its testing approach based on the system tools and libraries it detects, ensuring a thorough audit tailored to your infrastructure.
Practical Advantages for Lean Teams
For resource-strapped startups, Lynis is a lifesaver. Written entirely in shell script, it doesn’t require any additional software or dependencies. You can download it and begin auditing your systems almost immediately. After running, Lynis generates detailed reports that outline your security status and provide actionable recommendations to address potential vulnerabilities.
Michael Boelen, the creator of Lynis, highlights its simplicity and accessibility:
"Lynis is now a well-seasoned tool and known to many system administrators. Its stability and community are features that many like. The focus on simplicity and ease of use is another important aspect. Many hours went into simplifying the commands and use of parameters or configuration. Its lightweight footprint and the fact that Lynis is written in shell scripts make it usable on many systems."
The lightweight shell script design also makes Lynis compatible with containers, IoT devices, and NAS systems, offering flexibility for diverse environments.
Maximizing the Benefits of Lynis
To get the most out of Lynis, focus on custom configurations and regular audits. Customize the tool by adding specific tests or plugins and disabling overly strict checks that may not align with your startup’s needs. This approach allows you to enhance your security posture gradually, without overwhelming your team .
For startups managing multiple systems, Lynis plugins can provide deeper insights by collecting additional system information. Its ability to run on virtually any Unix-based system - from traditional servers to containers and IoT devices - makes it a versatile choice for varied tech stacks.
Regular audits with Lynis help you quickly identify and address security gaps. The detailed reports prioritize which vulnerabilities to tackle first, enabling you to make informed decisions about where to direct your limited resources. For startups aiming to strengthen their security without breaking the bank, Lynis offers a practical and scalable solution.
22. OpenVAS
OpenVAS (Open Vulnerability Assessment System) is a free, open-source platform designed to help startups identify and address security weaknesses without spending a fortune. Unlike tools that focus solely on configuration issues, OpenVAS scans your entire infrastructure, detecting vulnerabilities like outdated software, misconfigurations, and weak passwords.
For startups, the appeal of OpenVAS lies in its cost-free access to enterprise-level scanning capabilities. This makes it easier for smaller businesses to implement strong security measures without breaking the bank. Let’s break down its components and how they work together to deliver thorough scanning.
Understanding OpenVAS Architecture
OpenVAS relies on several components working in harmony. The OpenVAS Scanner identifies vulnerabilities using Network Vulnerability Tests (NVTs), while the Manager oversees configurations and manages scan results. For ease of use, the Greenbone Security Assistant (GSA) provides a web-based interface.
One of its standout features is the Greenbone Security Feed (GSF), which ensures scans stay up to date. Covering approximately 26,000 Common Vulnerabilities and Exposures (CVEs), OpenVAS delivers a comprehensive security assessment.
Practical Implementation for Startups
Setting up OpenVAS requires some technical expertise. Many startups choose to install it on a Kali Linux virtual machine for convenience.
Once installed, OpenVAS shines in automated scanning. You can schedule scans to run during off-hours, ensuring continuous security monitoring without interrupting daily operations. The tool also generates detailed reports, making it easy to share findings with team members or stakeholders.
For environments with multiple systems, OpenVAS supports authenticated scans by using credentials. This approach uncovers more vulnerabilities than basic network scans, revealing issues that external-only tools might overlook. After setup, startups can schedule regular scans to maintain ongoing security.
Maximizing OpenVAS Effectiveness
To get the most out of OpenVAS, focus on addressing high-severity vulnerabilities first. The reports generated by the system help prioritize these risks effectively.
OpenVAS also supports multi-user environments, allowing teams to collaborate while maintaining proper access controls through different permission levels.
Keep the software and vulnerability feeds updated to ensure scans remain accurate. The active OpenVAS community provides resources and updates, making it a reliable, long-term security solution for startups looking to grow securely.
23. Burp Suite Community Edition
Burp Suite Community Edition is a powerful, no-cost tool designed for web application security testing. Developed by PortSwigger, it acts as a bridge between your web browser and target applications, allowing you to intercept, analyze, and modify HTTP traffic. This capability helps identify vulnerabilities before malicious actors can exploit them, making it an invaluable resource for startups focused on securing their web applications.
With over 70,000 security professionals relying on Burp Suite worldwide, it’s a trusted choice for web application testing. For startups, this tool provides the means to implement effective security practices without stretching limited budgets. Let’s break down its core features and practical uses.
Understanding Burp Suite's Core Components
Burp Suite Community Edition offers several manual testing tools that are essential for identifying vulnerabilities:
- Burp Proxy: The backbone of the suite, it intercepts HTTP requests and responses between your browser and web servers, allowing you to examine and manipulate data in transit.
- Repeater: This tool lets you manually modify and resend HTTP requests to observe how your application handles various inputs.
- Decoder: Useful for working with encoded data, enabling you to decode or encode information as needed.
- Sequencer: Analyzes the randomness of session tokens, helping pinpoint weaknesses in authentication mechanisms.
It’s worth noting that the Intruder tool, which is included in the Community Edition, is rate-limited, making it less suitable for high-speed testing.
Setting Up Burp Suite for Your Startup
Getting started with Burp Suite requires a bit of configuration. First, set up your browser to route traffic through Burp’s proxy. Browser extensions like FoxyProxy can simplify this process. Next, install Burp’s certificate to inspect HTTPS traffic seamlessly. Once everything is configured, you can define a target scope to focus your testing efforts on specific domains or applications.
Practical Testing Strategies for Startups
Once your setup is complete, you can start testing by creating a site map of your web application. As you browse your app with Burp intercepting traffic, you’ll uncover its structure and may even find hidden endpoints that automated crawlers might overlook. Then, use the Repeater tool to manually test for vulnerabilities like SQL injection, cross-site scripting (XSS), and authentication bypasses by tweaking request parameters and observing the results.
While the Community Edition is robust for manual testing, it does have limitations. The rate-limited Intruder tool slows down brute-force testing, and there’s no automated vulnerability scanner like the one available in the Professional version.
Maximizing Value Within Budget Constraints
For startups operating on tight budgets, Burp Suite Community Edition offers plenty of value. While the Professional version costs €449, the free version allows for thorough manual testing of critical areas like authentication flows, session management, and input validation. You can also enhance its functionality by installing free extensions from the BApp Store through the Extender feature.
This tool is particularly well-suited for startups with team members who can dedicate time to manual security testing. By focusing on processes that don’t require automation, it becomes a key part of a broader manual vulnerability testing strategy, ensuring your web applications are as secure as possible without breaking the bank.
24. Hashcat
Hashcat is a powerful, open-source password recovery tool designed to help startups evaluate and improve password security. It's a smart choice for organizations working with limited budgets, offering a reliable way to assess password strength and recover lost credentials by cracking password hashes using advanced techniques.
What makes Hashcat stand out is its ability to handle over 350 hash types. From widely used algorithms like MD5 and SHA-1 to more secure options like bcrypt, it covers a broad spectrum. This flexibility allows startups to test password security across various systems and platforms.
Hardware Acceleration for Faster Results
Hashcat takes performance to the next level by utilizing hardware acceleration. Unlike older tools that rely solely on CPUs, Hashcat taps into the power of GPUs to significantly speed up the password-cracking process. This approach not only saves time but also enables thorough password audits without requiring expensive hardware upgrades. Plus, it's compatible with Linux, Windows, and macOS, making it easy to integrate into your existing setup.
Effective Password Testing Techniques
Hashcat offers multiple attack modes to identify weak passwords before they become a security risk. For instance:
- Dictionary attacks: Test passwords against common word lists for quick results.
- Rule-based attacks: Modify word lists by adding numbers, changing letter cases, or applying other patterns to mimic real-world password habits.
Starting with dictionary attacks is often the best approach since they are faster than brute-force methods and can uncover many weak passwords right away.
Crafting Better Password Policies
Regular testing with Hashcat can help shape stronger password policies for your startup. Experts suggest implementing rules that require passwords to be at least 12 characters long, include a mix of characters, and be updated regularly. Adding two-factor authentication (2FA) is another effective way to enhance security.
Tips for Smooth Operation and Maintenance
When using Hashcat for extended periods, it's crucial to monitor GPU temperatures to prevent overheating during intensive sessions. Keeping GPU drivers up to date ensures optimal performance and compatibility with the latest hash algorithms. If your startup uses cloud services like Azure AD, combining Hashcat's capabilities with built-in security features - such as Microsoft's block lists and custom password restrictions - can further strengthen your defenses. Additionally, tracking failed login attempts alongside Hashcat testing can help identify brute-force attacks early.
25. Gpg4win
Gpg4win is a free, open-source encryption software suite designed for Windows that uses OpenPGP. It allows you to encrypt and digitally sign emails, files, and other sensitive data through public-key cryptography, offering a reliable way to secure communications and information. Here's how Gpg4win simplifies encryption for emails, files, and compliance needs.
At its core, Gpg4win relies on public-key cryptography. You share your public key with others while keeping your private key secure. When someone wants to send you encrypted information, they use your public key to lock the data, and only your private key can unlock it.
All-in-One Security Solution
Gpg4win comes as a complete package, including tools like Kleopatra, GPA, GpgOL for Outlook, GpgEX for Windows Explorer, and Claws Mail. These tools are powered by GnuPG (GNU Privacy Guard), the encryption engine at the heart of the suite.
This setup makes it easy to encrypt files directly from Windows Explorer, secure emails in Outlook, and manage encryption keys - all within a single interface. For startups juggling multiple communication and file-sharing platforms, Gpg4win's integrated tools simplify the process of keeping data secure.
Email Encryption Made Easy
Gpg4win works seamlessly with popular email clients such as Microsoft Outlook and Mozilla Thunderbird. Once set up, encrypting and digitally signing emails becomes a quick and straightforward task. This ensures your recipients can verify the authenticity of your messages while keeping the content secure.
And it’s not just limited to email - Gpg4win also makes protecting sensitive files effortless.
Simple File Encryption
With Gpg4win, you can encrypt files and folders on your Windows system. Whether it’s customer data, financial documents, or proprietary information, encryption ensures that only authorized individuals can access these files. This is especially useful when dealing with lost or stolen devices or when sharing files through cloud storage.
Helping with Compliance
For startups navigating strict data protection regulations, Gpg4win offers more than just encryption. It helps ensure the confidentiality and integrity of sensitive information, supporting compliance efforts in industries with rigorous security requirements.
How to Get Started
To start using Gpg4win, download it from the official website. Use Kleopatra to generate your encryption keys and configure your email clients with the included plugins. Make sure to train your team on how to use the software and keep it updated regularly for optimal security.
26. VeraCrypt
When it comes to safeguarding sensitive data, startups need reliable and cost-effective cybersecurity tools. That’s where VeraCrypt steps in. This free, open-source disk encryption software allows users to create encrypted volumes and partitions, ensuring critical information stays protected. Unlike proprietary solutions, VeraCrypt’s open-source nature lets anyone inspect its code for vulnerabilities, offering peace of mind to startups prioritizing data security.
VeraCrypt is compatible with a wide range of platforms, including Windows (starting from XP), macOS, Linux, Raspberry Pi, and FreeBSD. This flexibility makes it an excellent choice for startups operating in diverse tech environments.
Three Ways to Encrypt Your Data
VeraCrypt provides three core encryption methods tailored to meet different needs:
- Encrypted file containers: Think of these as virtual safes. You create a file that acts as an encrypted disk. Once mounted with your password, it behaves like a regular drive where you can securely store sensitive files.
- Encrypt non-system partitions or drives: This includes external drives like USB sticks, offering portable protection for your data.
- Full system partition encryption: For maximum security, encrypt your entire system partition, ensuring the operating system and all files are safeguarded.
On-the-Fly Encryption
One standout feature of VeraCrypt is its on-the-fly encryption. This means data is automatically encrypted when saved and decrypted when accessed, without requiring manual intervention. Even metadata within a VeraCrypt volume is encrypted, ensuring comprehensive protection.
This seamless encryption process ensures your data is secure without disrupting your workflow.
Setting Up VeraCrypt
To get started, download VeraCrypt directly from its official website. During installation, select robust encryption algorithms like AES for top-tier protection.
Here are a few tips for setup:
- Use passwords that are at least 20 characters long for creating volumes.
- During volume creation, move your mouse randomly for about 30 seconds. This step adds entropy, making your encryption even more secure.
- If you’re encrypting a system partition, create a VeraCrypt rescue disk immediately. This disk can save you in case of boot issues.
Tips for Startup Teams
To ensure smooth operations, unmount VeraCrypt volumes when they’re not in use. For removable drives, confirm they’re formatted with NTFS for compatibility. Regularly update VeraCrypt to benefit from the latest security patches, and always handle encryption keys with care.
27. Rkhunter
Hidden threats can throw a wrench into a startup's operations. Rkhunter (Rootkit Hunter) is a free, open-source tool designed for Unix and Linux systems. It scans for rootkits, backdoors, and other concealed threats by comparing local files against known hashes and checking file permissions. For startups working with tight security budgets, Rkhunter can uncover vulnerabilities that traditional antivirus software might miss. Below, we’ll cover what Rkhunter checks, how to install it, run effective scans, and keep it accurate.
What Rkhunter Checks
Rkhunter dives deep into your system to uncover potential threats. It:
- Monitors critical system files for SHA256 hash changes.
- Scans for files commonly associated with rootkits.
- Flags executables with unusual file permissions.
- Searches for suspicious strings in kernel modules.
- Detects hidden files buried in system directories.
After each scan, it generates detailed reports that highlight any red flags and offer steps to address them.
Getting Started with Rkhunter
If you're using Ubuntu or Debian, getting started with Rkhunter is straightforward:
-
Install Rkhunter: Run
apt-get install rkhunter. -
Update the signature database: Use
rkhunter --updatebefore your first scan. -
Create a baseline: Run
rkhunter --propupdto establish a reference of trusted file properties.
Setting up a baseline is critical - it helps Rkhunter differentiate between legitimate changes and potential security issues.
Running Effective Scans
To make the most of Rkhunter, here are the key commands:
-
Run a full scan:
sudo rkhunter --check -
Show warnings only:
sudo rkhunter --check --rwo
Using sudo ensures Rkhunter has the necessary permissions to perform a thorough scan. For added convenience, you can automate scans by tweaking /etc/rkhunter.conf. Set your MAIL-ON-WARNING address to receive alerts, and enable daily scans by adjusting the CRON_DAILY_RUN and CRON_DB_UPDATE settings to "true" in /etc/default/rkhunter.conf.
Keeping Rkhunter Accurate
To maintain Rkhunter’s reliability, follow these steps:
-
Review logs: Check
/var/log/rkhunter.logafter each scan. -
Update your baseline: After system updates or software installations, run
rkhunter --propupdto prevent false positives. -
Whitelist trusted files: Add known safe files to
/etc/rkhunter.confto minimize unnecessary warnings. -
Pinpoint issues quickly: Use the command below to search for warnings in the logs:
sudo grep "Warning" /var/log/rkhunter.log
28. Fail2Ban
Brute-force attacks can bring a startup's servers to their knees in no time. Fail2Ban, a free and open-source intrusion prevention tool, acts as an automated watchdog for your server. It monitors log files in real time, identifies suspicious activity, and blocks brute-force attempts before they cause damage. Considering over 80% of website breaches involve brute force or stolen credentials, Fail2Ban is a must-have for startups without a dedicated security team.
How Fail2Ban Shields Your Server
Fail2Ban uses "jails", which are security modules designed for specific server services. Each jail keeps an eye on particular log files and applies rules to detect suspicious behavior. When it spots too many failed login attempts, it blocks the offending IP address by updating firewall rules automatically.
The tool dynamically adjusts firewall settings to deny access after a set number of failed attempts. It’s versatile enough to monitor a variety of services, including SSH, FTP, web apps, email systems, and databases. By imposing temporary bans, it ensures legitimate users aren’t permanently locked out while keeping attackers at bay.
Features That Matter for Startups
Fail2Ban comes packed with features that are especially helpful for startups working with limited security resources. Its automated IP blacklisting stops repeated offenders in their tracks, while customizable filters let you fine-tune monitoring for the services you rely on most.
Other handy features include email alerts for newly banned IPs and adjustable ban settings, allowing you to define thresholds like the number of failed attempts within a specific time frame. It integrates seamlessly with firewalls like iptables, firewalld, and UFW, and supports services such as SSH, HTTP, FTP, SMTP, and MySQL. A standout feature is the recidive jail, which tracks repeat offenders and enforces longer bans for persistent threats.
With these capabilities, properly configuring Fail2Ban can significantly bolster your startup’s defenses.
Getting Fail2Ban Up and Running
To deploy Fail2Ban effectively, start by configuring it to suit your needs. Create a jail.local file to set service-specific parameters like bantime, findtime, and maxretry. For instance, you might configure it so that three failed login attempts in a short period trigger a two-minute ban.
Whitelist trusted IPs using the ignoreip parameter to avoid accidental lockouts. Enable email notifications to stay updated on banned IPs, and keep an eye on logs to refine filters as new threats emerge. Testing your configuration thoroughly before going live is critical - missteps could either block legitimate users or fail to catch actual attacks.
Ongoing Monitoring and Maintenance
Once Fail2Ban is configured, regular monitoring is crucial to ensure it keeps up with evolving threats. Reviewing logs can reveal new attack patterns, helping you fine-tune thresholds and filters. You can also create custom filters to enhance detection for the specific services your startup uses.
If you’re using other security tools, Fail2Ban can integrate with threat intelligence platforms like blocklist.de and AbuseIPDB. This allows for real-time detection and mitigation of malicious activity, making it a valuable addition to your security toolkit.
Out of the box, Fail2Ban includes filters for widely used services like Apache, Lighttpd, SSH, vsftpd, and various mail servers, making it ready to protect most startup infrastructures with minimal setup effort.
29. Wazuh
For startups aiming to secure their operations without breaking the bank, Wazuh is a standout solution. This open-source platform combines threat detection, file integrity monitoring, and incident response into one cohesive system that evolves with your business needs. By analyzing data from agents deployed across your infrastructure, Wazuh identifies potential threats, sends alerts, and manages agent configurations - all while keeping tabs on their status. Its integrated approach forms the backbone of the specialized security modules outlined below.
Why Wazuh Stands Out for Startups
Wazuh tackles critical security challenges with features like File Integrity Monitoring (FIM) to track changes in essential files and configurations, a vulnerability detection engine that continuously scans for weaknesses, and log analysis tools to uncover key patterns. These capabilities also generate automated reports, simplifying compliance with regulatory standards.
Its versatility is another major plus. Wazuh agents are compatible with Windows, Linux, macOS, and Unix systems, while its central components are optimized for 64-bit Linux environments, ensuring efficient infrastructure management.
Deploying Wazuh Effectively
To make the most of Wazuh, start by identifying your most critical assets and deciding between a single-server or distributed setup. Integrating Wazuh with your existing security tools can help break down information silos and create a more cohesive security strategy. Customization is key - adjust agent settings, fine-tune rule sets to align with your environment, and set alert thresholds that minimize unnecessary noise while catching real threats. For startups anticipating growth, adopting a distributed architecture early on and allocating sufficient CPU, memory, and storage (with load balancing if needed) can help sidestep performance issues.
Keeping Wazuh Running Smoothly
Once Wazuh is up and running, regular maintenance is essential. Update the system frequently, but disable package repositories to avoid unintended upgrades. Use log rotation to manage storage effectively, and continually monitor performance to refine rule sets as new threats emerge. Staying proactive ensures your security setup scales seamlessly alongside your business.
With its powerful monitoring tools and zero licensing costs, Wazuh is a smart choice for startups seeking enterprise-level security without stretching their budgets.
30. Sysmon
Sysmon is part of Microsoft's Sysinternals pack. It's a no-cost tool for Windows that looks at when processes start, network ties, and changes to files, noting them down in the Windows Event Log.
Why Sysmon Is Key for Windows Startups
Sysmon fills big holes in Windows logs by giving a deep view of what's going on in the system. Security experts at Blumira stress how vital it is:
"Sysmon gives you deep visibility into every OS that's running in your environment, so you'll be able to say with high confidence that you know what your environment is doing, because you have all of the logs for it. Put simply: Sysmon will save your sanity during the IR process."
When you log key stuff like new tasks with full commands, file types (SHA1, MD5, SHA256, and IMPHASH), and net links (like where they come from, IP info, ports, and names), Sysmon helps you find threats faster than many old tools [\266](http://www.tetrain.com/blogs/post/104/best-practices-for-deploying-wazuh-tips-for-optimized-security.html).
Real-World Use of Sysmon
In early 2021, during the ProxyLogon and ProxyShell issues that hit Microsoft Exchange servers, Sysmon showed its value. Places with Sysmon saw early bad signs, like PowerShell code in DLLHost, checking admin rights, odd SMB use, and coded PowerShell lines [\269](https://igorsec.blog/2023/08/14/wazuh-part-2-installing-wazuh-and-configuring-the-server). These finds led to faster fixes than just using Windows' own logs. But, you need to set Sysmon right to get these wins.
How to Set Up Sysmon Right
To get the most from Sysmon, you must set it up right. Without good setup, the tool may make too much data, making your log system work too hard. XML config files let you pick what events to note, so you get just what you need for your startup [\266](http://www.tetrain.com/blogs/post/104/best-practices-for-deploying-wazuh-tips-for-optimized-security.html)[\268](https://documentation.wazuh.com/current/installation-guide/wazuh-server/index.html).
A good place to start is SwiftOnSecurity's free Sysmon config template. It gets updates often and you can change it to fit your safety needs and how you work.
To put Sysmon in, use PowerShell as Admin and do the install with -i and -accepteula [\272](https://documentation.wazuh.com/current/installation-guide/index.html). After that, fix max log sizes and set overwrite in the Event Viewer to keep storage okay. Then, mix Sysmon logs with your SIEM for full watch.
Mixing and Deep Watch
Sysmon's logs work best when put into a SIEM, turning basic data into useful info [\267](https://documentation.wazuh.com/current/installation-guide/index.html)[\273](https://documentation.wazuh.com/current/installation-guide/index.html). Running safe from most messing by users, Sysmon stays trustworthy even if things go wrong [\266](http://www.tetrain.com/blogs/post/104/best-practices-for-deploying-wazuh-tips-for-optimized-security.html). It also notes stuff from when the system starts, spotting deep bad software that might trick other tools.
For startups using Windows, Sysmon gives big-league watch without big costs, so it's key for your safety tools.
Tool Guide Chart
Picking the best no-cost safety tools is key for new small businesses working with less, but still seeing big online risks. Below is a chart that splits up different tools into main groups. This helps you see which tools match your startup's needs. Each tool focuses on its own safety issues and differ in what they offer, how easy they are to use, and their good points.
| Tool Type | Tool Name | Main Features | Rules Met | Good for Startups | Easy to Learn |
|---|---|---|---|---|---|
| Password Keeping | Bitwarden | Open-code, group vaults, 2FA help | SOC 2, GDPR rules | No pay for small groups, simple safe plan | Easy – clear use |
| KeePass | Keep in place, high safe code, add-ons | Self-run fits most setups | You hold all data, pay nothing each month | So-so – needs set up | |
| Check for Flaws | OpenVAS | Scan the network, test with real sign-in | NIST CSF, ISO 27001 in line | No pay big-level scanning | Hard – setup is a lot |
| Trivy | Safe for bins, works in CI/CD | Fits DevSecOps rules | Made for new work steps | Easy – use with simple commands | |
| Nikto | Scan web host, can add more code | Tests for OWASP rules | Fast check on web safe | So-so – need to know web safe | |
| Watch the Network | Zeek | See all traffic now, can script | Fits NIST rules | See deep into network for any bad signs | Hard – need to know network well |
| Wireshark | Catch packs, check protocols | Fits rules for looking back | Top tool to find network problems | So-so – big but tricky | |
| Safe Talking | Signal | Codes end to end, messages can vanish | Meets privacy rules | Easy, safe chats for key talks | Easy – works like any chat |
| Gpg4win | Make emails safe, digital signs | Fits FISMA, HIPAA for emails | Pro safe talking | So-so – need to manage keys | |
| Watch Systems | OSSEC | Look for breaks, check logs | Fits PCI DSS, HIPAA rules | See all safety stuff at once, on all platforms | Hard – many configs |
| Wazuh | Has SIEM, sticks to many rules | SOC 2, PCI DSS, HIPAA, GDPR | Full fix for safe ops | Hard – big back-end needs |
Big Things to Think About for Startups
Data hacks can wreck startups, costing a lot - from $120,000 to $1.24 million. Using free tools can cut these risks. But some open tools need a lot of work and money. At times, these costs are as high as paid tools.
For startups in strict fields, rules like HIPAA and SOC 2 are a must. Tools like Bitwarden, OSSEC, and Wazuh match these rules well. The NIST Cybersecurity Framework is a strong base for any safety plan.
Ease of use is big for startups with few IT folks. Tools like Bitwarden and Signal are simple to start and offer quick safety. But, tools like OpenVAS and Zeek take more time and know-how.
Fitting in and growing matter too. For example, Sysmon logs fit well with Wazuh for checking Windows. Trivy works well in Docker setups. As your business grows, tools like Wazuh can do more, from simple log checks to full SIEM jobs, while simple tools like KeePass might not work for big teams.
Think about your team's skills too. If you have good security pros, you can use complex tools like Zeek or OpenVAS. But with no full-time security folks, choose easy tools that protect well without a lot of set-up or learning.
Your need to follow rules can steer your choices. Say if SOC 2 is urgent, pick tools that help with audits first. For plans that can wait, you might look at deeper solutions for wider safety.
How to Deploy Free Security Tools in Startups
Setting up free security tools in a startup is more than just adding programs - it's about planning a fit that works for your team’s size, money, and rules. Here is a simple guide to help you start using these tools right.
Begin with a Security Plan
Before you start adding things, make a security map. It should show your key items, who can get to them, and how you will deal with dangers. Focus on the big risks to make sure you're not using tools that don’t really help. Also, it's often less costly to stop a problem than to fix it later.
Look at your top items - like customer info, money records, or new ideas. They need the best safety. For instance, if you deal with payments, start with tools like Zeek or Suricata for watching the network before you add more general tools.
Put Tools in Place Bit by Bit
Putting in many tools at once can be too much for your team. Instead, add them bit by bit, starting with what’s most important and what your team can manage.
- First Part: Start with simple things like password keepers (e.g., Bitwarden) and safe chat apps (e.g., Signal) for quick gains.
- Second Part: Then, add tools for seeing the network and checking for weak spots, such as Wireshark for problem-solving and Trivy for keeping containers safe.
- Third Part: After the basics, go to more complex tools like OSSEC, Wazuh, or Security Onion for watching and dealing with issues.
Make Tools Part of Daily Work
For these tools to work well, they must fit smoothly into your team’s daily tasks. For example, if you use CI/CD pipelines, add Trivy scans to the building steps.
If you work with outside rule, risk, and rule (GRC) services like Cycore, line up your tool setup with rule needs. Many free tools, like OSSEC, can send data straight to rule systems, making checks simpler. For example, OSSEC logs can help with SOC 2 needs, while Wazuh’s logging helps with HIPAA rules.
Handle the Setup Need
Free tools often need more setup than paid ones. Plan for a step-by-step setup process that covers adding, testing, and writing it down. Here’s a common plan:
- Week 1: Put in and test the tool in a safe place. Find any problems.
- Week 2: Start using the tool a little in real work. Watch how it does and adjust as needed.
- Week 3: Use it more across the team and teach the basics.
- Week 4: Start keeping routines and make the tool a part of your daily work.
For more complex tools like OpenVAS or Zeek, this plan might take six to eight weeks. Take your time - going too fast can cause wrong setups, which may lead to wrong alerts or missed dangers.
Grow a Safety-First Mindset
Even the best tools won't help if your team doesn't use them right. Give short, simple training to show your team how to use each tool. For example, teach them to make strong passwords with a manager or find odd things in network screens.
Don't go for long workshops, but hold short monthly talks about common dangers like phishing and show how your tools stop them. This keeps security in mind but doesn't overload your team.
Keep Tools Updated and Maintained
Free tools may need more updates than paid ones. Plan regular updates for software fixes and signature files. For example, ClamAV might need daily updates, but tools like Nmap might only update when a new version comes out.
Make clear steps for acting on alerts from tools like Suricata or OSSEC. Check each tool often to make sure it still fits your needs.
Align Deployment with Compliance Needs
If your startup has to meet audit or compliance rules, set up your tools with this in mind. Tools like Wazuh and OSSEC can handle a lot of the report work, but they need time to collect base data before audits.
Work with your GRC provider to see which tool results match your compliance needs. Many tools can give out logs in forms that work with compliance setups, saving time and keeping things consistent. Setting up one place for all logs early, using tools like Wazuh, makes a single point for reports and helps link events across systems.
Overcome Resource Challenges
Free tools can take a lot of effort to set up. Start with tools that are big-impact but easy to maintain like password managers and safe message apps. For harder tools, like Security Onion or OpenVAS, think about using cloud spots for scans instead of full-time gear. This way saves money but still keeps security strong.
Write down each step. Good records mean that even if team changes happen, the tools work well. Note not just how to use each tool but also why you picked it and the dangers it deals with.
Conclusion
Free safety tools are key for new small firms wanting to build strong safety without spending too much money. With almost half of cyberattacks aiming at small, less rich firms and about 60% of them closing within half a year of an attack, using these tools is not just smart - it's vital to stay up and running.
The 30 tools we talked about in this guide help in different ways to keep your online setup safe. From keeping passwords safe with Bitwarden to watching over networks with Zeek, these tools cover urgent safety needs. They find weak spots, make network safety stronger, and guard startups from the daily risks they face. Since data breaks can cost small firms a lot of money, these free options help lessen dangers.
But safety isn't just to stop bad things - it's key for growth. Good safety habits make customers, partners, and money givers trust you more. They help you get bigger deals and more money, making safety a must as your business grows. Using your tools as per rules, like SOC 2 for big clients or HIPAA for health data, can also lead to approvals that up your trust level.
As Ayman Elsawah, vCISO at Sprinto, wisely says:
"Delaying security measures costs not just money, but also valuable time and resources".
With that in mind, using many tools and guiding a startup can be too much at once. This is where hiring outside security help can really make a big difference. Working alongside pros lets you drop the hard parts of compliance and safety while you work on making your business bigger. By mixing no-cost tools with outside know-how, startups can get quick safety and build a good base for long-lasting growth.
FAQs
How should new small companies pick free safety tools to start with?
Where to Start on Safety for New Small Companies?
New small companies need to begin their safety work by finding their big risks and urgent needs. They should pick tools that handle important areas like scanning for weak spots and watching the network - these are key to find and fix dangers early.
Some tools many use are OpenVAS for checking where weak spots are, Nmap for studying the network, and Snort for spotting dangers in real time. These tools give a good base for making a safe place.
After setting up these key tools, new small companies can go into tools made for safe talking or following rules, as they need. Starting with these main tools helps them make their safety stronger without using up too many things.
How can free security tools help small new firms meet rules like SOC 2 or HIPAA?
Free security tools are key for helping small new firms meet rules like SOC 2 or HIPAA. They give must-have help such as checking for weak spots, finding threats, and keeping an eye on security - all for free. These tools make it easy for new firms to set up the needed security steps these rules ask for, cutting the cost of meeting these rules.
By doing tasks like risk checks, writing about security, and keeping watch all the time, these tools make the rule-following steps simpler. This way, new firms can save time and effort while they make sure they follow the rules, letting them focus on making their business big without losing out on security.








































































































