
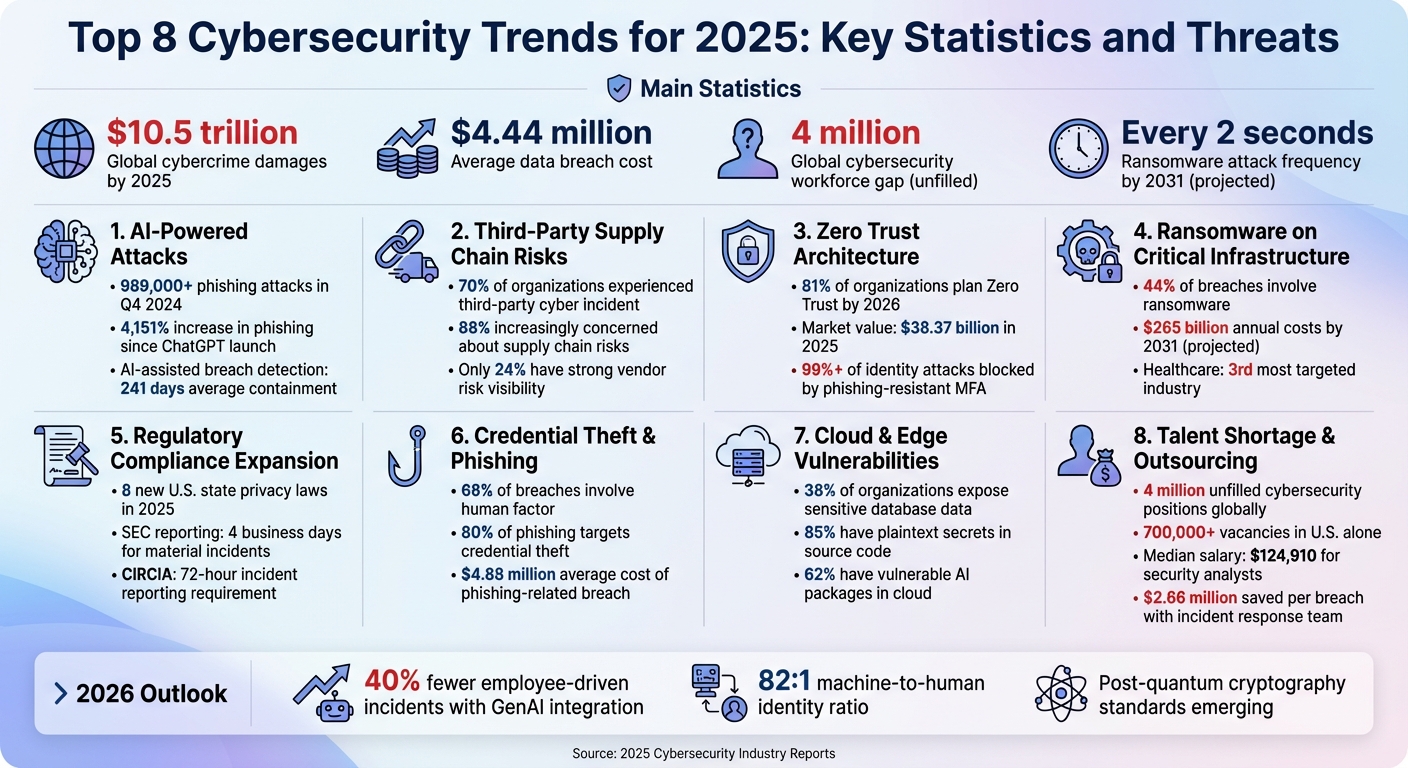
In 2025, cybersecurity shifted its focus from prevention to resilience, emphasizing preparedness for inevitable breaches. Key trends include AI-driven threats, third-party risks, and the rise of Zero Trust architecture. Compliance requirements are expanding, with stricter regulations like SEC's Regulation S-P demanding faster incident reporting. Meanwhile, ransomware attacks increasingly target critical infrastructure, and the talent shortage is driving companies to outsource security. Here's a quick overview:
- AI Threats: Generative AI is powering phishing, deepfakes, and malware, making attacks more sophisticated.
- Third-Party Risks: Supply chain vulnerabilities are a weak link, with continuous monitoring becoming essential.
- Zero Trust: Default-deny approaches are replacing outdated security models to combat credential theft.
- Ransomware: Attacks on critical infrastructure are growing, with damages projected to exceed $265 billion annually by 2031.
- Compliance: New regulations like GDPR updates and post-quantum cryptography mandates are reshaping security standards.
- Cloud Vulnerabilities: Neglected assets and machine identity gaps are exposing businesses to data breaches.
- Talent Shortage: With 4 million unfilled cybersecurity jobs globally, companies are turning to managed services.
Looking ahead to 2026, expect autonomous AI systems, stricter AI governance, and a shift toward protecting unstructured data like text and video. Cyber resilience and proactive strategies will be critical in navigating the evolving threat landscape.
Top 8 Cybersecurity Trends for 2025: Key Statistics and Threats
1. AI-Powered Attacks Require Stronger Defenses
Impact on Cybersecurity Practices
AI has reshaped the way cyberattacks unfold. Hackers are no longer limited to exploiting software vulnerabilities - they now use AI to automate entire attack processes and craft highly convincing social engineering schemes. Tools like WormGPT have made it easier for even inexperienced criminals to launch attacks that once required advanced skills.
Take phishing, for example. AI is being used to mimic corporate writing styles, making these scams harder to detect. In Q4 2024 alone, over 989,000 phishing attacks were reported. One alarming case involved a finance employee at a global company who was tricked into transferring $25 million during an AI-generated virtual meeting.
On the defense side, organizations using AI tools are seeing real progress. Companies employing AI for threat detection have managed to identify and contain breaches in an average of 241 days - the best performance in nearly a decade. By 2026, businesses integrating AI with advanced security platforms are expected to reduce employee-related incidents by 40%. These advancements highlight the importance of integrating AI into security frameworks early on.
Alignment with Compliance Frameworks (e.g., SOC 2, ISO 27001, GDPR, HIPAA)
As AI evolves, compliance standards are adapting to keep up. Meeting regulatory requirements now involves embedding AI-driven security measures from the start. Frameworks such as SOC 2 and ISO 27001 emphasize incorporating governance and risk controls into AI systems during their development. This "secure-by-design" approach is becoming the norm for audits.
The focus of compliance is also shifting. Alex Michaels, Senior Principal Analyst at Gartner, notes:
"The rise of GenAI is transforming data security programs, shifting focus to protect unstructured data - text, images and videos."
Historically, compliance strategies centered on structured databases. But AI systems depend on unstructured data like text, images, and videos, which are often less secure. For GDPR compliance, many organizations are now using synthetic data for AI training to safeguard privacy and reduce bias.
Relevance to Emerging Threats and Trends
The pace of new threats is outstripping the ability of many security teams to respond. One growing danger is "Agentic AI" - malicious AI capable of independently navigating networks and executing multi-step attacks without human input. These AI agents operate at machine speed, adapting their strategies in real time based on the environment they encounter.
Deepfakes are another rising concern. By 2025, 8 million video and voice deepfakes are expected to circulate globally. Cybercriminals use these for scams like pig butchering, market manipulation, and bypassing biometric security systems. The 2025 FINRA Regulatory Oversight Report specifically highlights the risks of GenAI being weaponized for market fraud.
The financial toll is staggering. Global cybercrime damages are projected to hit $10.5 trillion by 2025, with the average data breach costing $4.44 million. Businesses can’t afford to treat AI-driven attacks as a distant threat - they’re already here.
Practicality of Implementation for Businesses
AI is proving invaluable in addressing the cybersecurity talent shortage. Over half of organizations (53%) are prioritizing AI and machine learning to fill gaps in expertise. By 2025, AI will top the list of cybersecurity investment priorities for security leaders, allowing limited teams to focus on proactive tasks like threat hunting instead of drowning in alerts.
Many businesses are opting for targeted AI solutions, or "Tactical AI", which focus on specific, high-impact use cases[1,4]. This includes tools for automated phishing detection and real-time monitoring of cloud misconfigurations. The concept of "SOC 2.0" - Security Operations Centers powered by AI automation - is gaining traction, with AI agents managing routine alerts autonomously. Industry leaders like Mayo Clinic and JPMorgan Chase have successfully implemented AI-driven zero trust models, proving these strategies can work on a large scale.
2. Third-Party Supply Chain Risks Increase
Impact on Cybersecurity Practices
AI-driven attacks are pushing organizations to rethink their cybersecurity strategies, but the threats don’t stop at internal defenses. External vulnerabilities in supply chains are becoming just as critical. In fact, over 70% of organizations reported a major third-party cyber incident in the past year, and 88% are now increasingly concerned about these risks.
Cybercriminals have adjusted their tactics, targeting key vendors that serve entire industries. Why attack hundreds of companies when breaching one vendor can disrupt an entire network of clients? This shift has made continuous monitoring of vendors a necessity. As Morgan Adamski, Principal at PwC US, points out:
"Traditional risk assessments fall short; continuous monitoring is essential to detect and respond in real time."
Despite these challenges, only 24% of organizations feel they have strong visibility into vendor risks, and fewer than half monitor even half of their extended supply chain for threats. The problem extends deeper: most companies lack insight into their suppliers’ suppliers, with only 34% confident that third parties would notify them of a breach. These gaps in visibility demand a more proactive approach, as the next section on compliance frameworks explores.
Alignment with Compliance Frameworks (e.g., SOC 2, ISO 27001, GDPR, HIPAA)
The growing risks in supply chains are driving changes to regulatory frameworks. By mid-2026, more than 80% of global enterprises are expected to fall under some form of AI or cybersecurity governance.
| Compliance Framework | Focus on Supply Chain Security |
|---|---|
| CMMC 2.0 | Requires DoD contractors to secure sensitive unclassified information shared with subcontractors. |
| DORA / NIS2 | European regulations emphasizing digital resilience and strict supply chain security enforcement. |
| NIST PQC Standards | Aims to guide supply chains in adopting quantum-safe cryptography. |
| GDPR | Enforces stringent penalties for breaches involving third-party processors or unlawful data transfers. |
Frameworks like SOC 2 and ISO 27001 now emphasize automated access reviews and continuous vendor control monitoring. GDPR has introduced requirements for detailed data flow mapping to track how third-party vendors handle sensitive information. For healthcare organizations, ensuring Business Associate Agreements (BAAs) and securing medical supply chains are critical to meet HIPAA standards.
Michael Rasmussen, GRC Analyst at GRC Report, highlights the importance of collaboration:
"Third-party risk cannot be managed in isolation. Operating in silos - where departments work independently with no cross-functional collaboration - creates gaps in visibility and accountability."
On average, organizations now dedicate 11 working weeks annually to compliance tasks.
Relevance to Emerging Threats and Trends
The nature of supply chain risks is evolving, with identity-based and AI-related threats taking center stage. Machine identities now outnumber human accounts by a staggering 82:1. Instead of breaking in, attackers are "logging in" by exploiting vendor identities or session tokens to bypass MFA protections.
Jane Frankland MBE, a Cybersecurity Leader, warns:
"The gap between vulnerability disclosure and exploitation is virtually gone... new CVEs can be weaponized within 15 minutes of publication."
AI technologies embedded in supply chains introduce new risks like prompt injection and data poisoning, where adversaries manipulate AI models or training data. Alex Michaels, Senior Principal Analyst at Gartner, underscores the urgency:
"SRM leaders now have clear responsibilities to secure third-party AI consumption, protect enterprise AI applications, and improve cybersecurity with AI."
Ransomware attacks targeting supply chain partners have surged, growing 34% year-over-year in 2025. Attackers are using double and triple extortion tactics to amplify disruption, with the average cost of a U.S. data breach reaching $10.22 million in 2025. Additionally, quantum cryptography migration mandates are pushing critical infrastructure providers to map their cryptographic dependencies, ensuring compliance by 2026.
Practicality of Implementation for Businesses
Addressing these risks doesn’t mean overhauling your entire security stack. Practical steps like implementing Software Bills of Materials (SBOMs) help track software dependencies and quickly identify vulnerabilities within the supply chain.
Vendor contracts should include clear cybersecurity benchmarks, such as encryption standards, incident disclosure requirements, and regular security testing. This is becoming increasingly important as 65% of organizations report that customers, investors, and suppliers now demand proof of compliance.
Network segmentation is another effective measure to contain potential breaches. By isolating mission-critical systems from external vendor networks, you can limit the damage caused by a supply chain attack. Additionally, joint incident response planning, including tabletop exercises, ensures coordinated responses to breaches. Unfortunately, only 26% of organizations incorporate incident response into their third-party risk management programs.
For stretched security teams, automation offers relief. Automating tasks like user access reviews and security questionnaires can save 3–5 hours per week, with 72% of IT leaders identifying automation as critical for optimizing time and resources.
Lastly, establish firm policies to pause or terminate vendor relationships that fail to meet security standards. The focus is shifting from trying to prevent every breach to building resilience that minimizes the impact when incidents occur.
3. Zero Trust Architecture Is Now Required
Impact on Cybersecurity Practices
The days of the "castle-and-moat" security model - trusting everything inside the network - are over. By 2025, 81% of organizations plan to implement Zero Trust by 2026, and the market for Zero Trust solutions is projected to reach $38.37 billion this year. Attackers have shifted tactics, often gaining access through stolen credentials.
Zero Trust flips the script with a "default-deny" approach. It continuously verifies every user, device, and application, ensuring no one is trusted by default. Micro-segmentation is a key feature, limiting the damage caused by breaches. If one segment is compromised, attackers can’t easily move across the network to access sensitive data.
This architecture is particularly valuable for remote work, where traditional VPNs and firewalls fall short. Companies are replacing outdated tools with Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE), which provide secure, identity-based access with granular permissions.
Alignment with Compliance Frameworks (e.g., SOC 2, ISO 27001, GDPR, HIPAA)
Zero Trust isn’t just about better security - it’s increasingly a compliance necessity. Standards like SOC 2 and ISO 27001 now emphasize detailed access controls, which are core to Zero Trust. Similarly, regulations like GDPR and HIPAA require strict identity-driven data protections for sensitive information.
The stakes are high: 47% of organizations report that missing compliance certifications delays their sales, and 38% have lost deals due to inadequate security assurances. Cyber insurance providers are also raising the bar, requiring organizations to demonstrate Zero Trust controls like phishing-resistant multi-factor authentication (MFA), access logs, and incident response plans. Phishing-resistant MFA alone blocks over 99% of identity-based attacks . On average, security teams spend eight hours weekly on manual compliance tasks.
By addressing compliance challenges, Zero Trust also helps mitigate emerging risks tied to identity theft and supply chain vulnerabilities.
Relevance to Emerging Threats and Trends
Identity-related attacks surged by 32% in the first half of 2025, with 97% relying on password-based methods. The explosion of machine identities - spanning GenAI tools to IoT devices - has introduced new risks. Shockingly, IAM teams manage only 44% of machine identities today.
Laiba Siddiqui, SEO Writer at Splunk, explains the essence of Zero Trust:
"The idea behind zero trust is simple: don't trust anyone or anything automatically. Just because someone's inside your network doesn't mean they should have access to everything."
Supply chain attacks further highlight the importance of Zero Trust. By 2025, 45% of organizations are expected to face supply chain cyberattacks - a threefold rise since 2021. Zero Trust ensures no third-party vendor or partner gains automatic access, requiring verification for every request.
Industries like healthcare and finance are leading the charge. For example, Mayo Clinic adopted an AI-driven Zero Trust model to safeguard patient records and monitor medical devices. Their approach mandates identity verification for all staff.
Practicality of Implementation for Businesses
Implementing Zero Trust doesn’t require ripping out your entire security infrastructure. A phased approach works best: start by focusing on your most critical assets and high-risk user groups. With enterprises using an average of 45 different cybersecurity tools, consolidating and validating existing systems is a logical first step.
Expand your identity and access management (IAM) to include both human and machine identities, such as IoT devices and AI workloads. Phishing-resistant MFA should be a priority, alongside conditional access policies that verify users and devices before granting access.
AI-powered network segmentation is another key step. It isolates sensitive data and replaces outdated VPNs with ZTNA solutions, which grant application-level access based on identity and context .
For businesses with limited security staff - where over half have one or fewer full-time security employees - automation is a lifesaver. AI tools can monitor access patterns, flag anomalies, and streamline compliance tasks in real-time, reducing reliance on manual processes.
As Zscaler warns:
"In 2025, organizations that do not adopt zero trust architecture will be increasingly vulnerable to breaches and ransomware attacks, because traditional castle-and-moat security is ineffective at protecting against evolving threats in the world of cloud and AI."
Adopting Zero Trust strengthens defenses while simplifying compliance, making it a critical strategy in today’s ever-changing threat landscape.
4. Ransomware Attacks Focus on Critical Infrastructure
Impact on Cybersecurity Practices
Ransomware is no longer just a digital threat - it’s now targeting the physical systems that keep critical infrastructure running. By 2025, 44% of analyzed breaches are expected to involve ransomware, with attacks predicted to strike a business, consumer, or device every 2 seconds by 2031. The financial toll is staggering, with global costs projected to surpass $265 billion annually by 2031.
What’s particularly alarming is how ransomware tactics have shifted. Instead of relying heavily on malware, 79% of adversary detections now involve malware-free methods like stolen credentials and legitimate system tools. This approach allows attackers to sidestep traditional defenses, targeting critical areas like energy grids, water supplies, and healthcare systems. These aren’t just data breaches - they’re threats with real-world, physical consequences.
The blending of operational technology (OT) and information technology (IT) has made critical infrastructure even more vulnerable. Once confined to corporate networks, these threats now extend to vital systems, amplified by AI-driven attacks and supply chain vulnerabilities. Nation-state actors, such as the group "Volt Typhoon", are embedding malicious code into infrastructure, shifting their goals from financial extortion to potential sabotage. In early 2025, the LockBit group introduced "LockBit 4.0", a ransomware variant tailored to attack private sector infrastructure in the U.S., using aggressive multi-stage extortion tactics.
Relevance to Emerging Threats and Trends
Healthcare has emerged as the 3rd most targeted industry for ransomware attacks, with devastating consequences. In February 2024, Change Healthcare, a subsidiary of UnitedHealth, experienced a ransomware attack that disrupted healthcare payments across the U.S. for weeks, costing the company an estimated $1.6 billion. They ultimately paid a $22 million ransom to regain control. Similarly, in June 2024, a ransomware attack on Synnovis forced seven major London hospitals to cancel over 800 surgeries and 700 outpatient appointments in just one week.
Attackers are also leveraging advanced tools like AI-powered "vishing" (voice phishing) and deepfake technology to bypass authentication. In one 2025 case, cybercriminals used deepfake video to impersonate a Chief Financial Officer during a video call, tricking an employee into transferring $25.6 million. Meanwhile, the China-linked group "Salt Typhoon" infiltrated major telecommunications networks in 2025, highlighting how critical infrastructure is increasingly targeted for both financial gain and geopolitical leverage.
Practicality of Implementation for Businesses
To counter these evolving threats, businesses must prioritize network segmentation. Keeping OT systems separate from IT networks is essential to prevent ransomware from spreading to physical control systems. This is particularly crucial for sectors like utilities, manufacturing, and healthcare, where downtime can have life-threatening consequences.
Tabletop exercises are another key strategy. These simulations, involving executives and board members, test response protocols for high-stakes scenarios like supply chain breaches - which now cost an average of $4.91 million per incident. Additionally, businesses should demand that third-party partners provide proof of secure software development practices and conduct thorough risk assessments of their suppliers.
Expanding identity and access management (IAM) strategies to include machine identities - such as service accounts, IoT devices, and AI workloads - is also critical. These are common entry points for attackers attempting lateral movement within networks. With 63% of organizations now refusing to pay ransoms (up from 59% in 2024), resilience planning is no longer a luxury. As Gartner puts it:
"Cyber resilience embraces a 'when, not if' mentality, and seeks to minimize the impact of cyber incidents on the enterprise and enhance adaptability".
5. Regulatory Compliance Requirements Expand
Impact on Cybersecurity Practices
Regulatory compliance is reshaping how businesses build and manage their security programs. By 2025, eight U.S. states - Delaware, Iowa, Minnesota, Maryland, Nebraska, New Hampshire, New Jersey, and Tennessee - will roll out new privacy laws. These state-level regulations are forcing companies to rethink their approach to customer data, especially as states like Texas and Connecticut ramp up enforcement efforts by staffing dedicated teams and removing mandatory cure periods for violations.
Regulators are also raising the bar for risk management. For example, the SEC's Regulation S-P now requires companies to have formal incident response programs in place, with specific compliance deadlines like December 2, 2025. Similarly, the HHS has updated the HIPAA Security Rule to mandate encryption of electronic protected health information (ePHI) both at rest and during transmission.
Alignment with Compliance Frameworks (e.g., SOC 2, ISO 27001, GDPR, HIPAA)
Certifications like ISO 27001 can help ease the burden of meeting new compliance requirements. However, businesses are finding it challenging to keep up with the increasing speed and specificity of reporting mandates. For instance:
- Public companies must report material cybersecurity incidents to the SEC via Form 8-K within four business days.
- Critical infrastructure entities under CIRCIA need to report cyber incidents to CISA within 72 hours and ransomware payments within 24 hours.
The SEC has also clarified that "materiality" should be assessed quickly, focusing on whether a reasonable investor would find the information important. These updates reflect how U.S. regulations are aligning with global standards, such as GDPR, to create a more uniform compliance landscape.
Relevance to Emerging Threats and Trends
New threats are driving regulators to tighten their requirements. AI-driven fraud, including deepfakes and automated attacks, has led to mandates for "secure-by-design" principles in high-risk AI systems. Colorado's AI Act, set to take effect in February 2026, and California's automated decision-making rules are targeting AI applications in areas like employment, lending, and healthcare.
Regulators are also cracking down on off-channel communications - business messages sent through unapproved platforms like WhatsApp. Financial institutions are now required to retain and archive these communications.
Additionally, data broker restrictions are expanding. The Protecting Americans' Data from Foreign Adversaries Act and the DOJ's final rule under Executive Order 14117 restrict the sharing of bulk sensitive personal data with certain "countries of concern". State regulators are increasingly requiring Data Protection Impact Assessments (DPIAs) for high-risk processing activities, such as targeted advertising, signaling a shift toward proactive risk management.
These evolving mandates are becoming a crucial part of the broader strategy to counter emerging cyber threats.
Practicality of Implementation for Businesses
To navigate these new regulations, businesses should:
- Update incident response plans to meet the SEC's four-day and CIRCIA's 72-hour reporting deadlines.
- Conduct asset inventories to ensure ePHI is properly managed and protected.
- Review vendor contracts to confirm data protection measures and clear incident notification responsibilities across all vendor tiers.
- Perform Data Protection Impact Assessments for processing activities involving sensitive data or targeted advertising, as required by state regulators.
Many organizations are turning to Trust Management Platforms to streamline compliance tasks like evidence collection, policy management, and remediation across frameworks such as SOC 2, ISO 27001, and HIPAA. With over half of businesses (53%) prioritizing AI and machine learning to address cybersecurity gaps, automation is becoming a key tool for staying ahead in an increasingly complex compliance environment.
sbb-itb-ec1727d
6. Credential Theft and Phishing Attacks Grow
Impact on Cybersecurity Practices
Cybercriminals are shifting their focus from exploiting system vulnerabilities to stealing legitimate credentials, fundamentally altering how organizations approach cybersecurity defense.
The statistics paint a worrying picture. Phishing attacks have skyrocketed by 4,151% since the launch of ChatGPT in late 2022. With the human factor contributing to 68% of all cybersecurity breaches, and 80% of phishing campaigns aimed specifically at credential theft, the stakes are higher than ever. When these attacks succeed, the financial toll is staggering - $4.88 million was the average cost of a phishing-related data breach in 2024.
Attackers are now using AI to generate phishing emails with impeccable grammar, making traditional "red flag" detection methods nearly obsolete. On top of that, advanced tactics like Adversary-in-the-Middle (AiTM) attacks are becoming more common. Kits like Tycoon 2FA and Sneaky 2FA use encrypted scripts to capture credentials and session tokens in real time, effectively bypassing multi-factor authentication (MFA).
One particularly alarming incident occurred in early 2024 when the Hong Kong subsidiary of engineering firm Arup lost $25.6 million. A finance employee was deceived during a video conference call where deepfake AI impersonations replaced every other participant.
This evolving threat landscape is driving the development of novel phishing methods, which are explored in the next section.
Relevance to Emerging Threats and Trends
The rise of credential theft has given birth to new phishing techniques like quishing and ClickFix, further complicating cybersecurity efforts. Quishing - phishing through QR codes - has grown by 25% year-over-year. Alarmingly, 17% of attacks bypassing spam filters now incorporate QR codes, with 89% of these targeting credential theft. Meanwhile, ClickFix tricks users into pasting malicious PowerShell scripts disguised as technical fixes into their systems.
Attackers are also exploiting trusted platforms like OneDrive, SharePoint, and DocuSign to deliver malicious content, effectively bypassing allowlists and reputation-based security measures.
Cybercrime is becoming more industrialized. Phishing-as-a-Service (PhaaS) kits are expected to account for 50% of credential theft attacks by 2025, up from 30% in 2024. These kits, available on the dark web and Telegram for as little as $350 per month, enable even inexperienced actors to launch sophisticated phishing campaigns.
Machine identities, such as API keys, OAuth tokens, and service accounts, are also becoming prime targets as organizations increasingly rely on automated environments. Shockingly, IAM teams currently manage only 44% of an organization’s machine identities, leaving a significant gap in security.
These evolving threats demand a shift in how businesses approach cybersecurity.
Practicality of Implementation for Businesses
To counter these threats, organizations need to adopt more advanced security measures. Start by implementing phishing-resistant MFA solutions. Transition from SMS or push-based authentication to FIDO2-compliant hardware keys, such as YubiKeys, which can thwart AiTM attacks. This is particularly critical in sectors like energy, mining, and oil/gas, where nearly 1 in 3 authentication attempts is flagged as a threat.
Replace outdated annual compliance training with Security Behavior and Culture Programs (SBCPs) that focus on real behavior change. Companies integrating AI into these programs are projected to see 40% fewer cybersecurity incidents caused by employees by 2026. Frequent phishing simulations - every 10 days - can reduce successful phishing attempts by up to 86%.
Leverage AI-powered detection platforms to spot unusual communication patterns and AI-generated phishing messages. Traditional defenses are no longer enough, especially since 94% of malware is still delivered via email attachments, and 80% of phishing websites now use HTTPS.
Finally, establish a unified strategy to manage non-human identities, such as API keys and service accounts. As attackers increasingly target these machine credentials, securing them is essential to closing critical gaps in your organization’s defenses.
7. Cloud and Edge Security Vulnerabilities Expand
Impact on Cybersecurity Practices
The numbers paint a stark picture: nearly one-third of cloud assets are neglected, each averaging 115 vulnerabilities. Even more alarming, 38% of organizations expose sensitive data in their databases, with the healthcare sector leading the way at a staggering 51% exposure rate. These vulnerabilities are forcing organizations to rethink their security strategies.
Consider this: 85% of organizations have plaintext secrets embedded in their source code repositories. Meanwhile, in cloud environments, machine identities - like API keys, service accounts, and OAuth tokens - outnumber human identities by a staggering 50 to 1. Yet, IAM teams oversee only 44% of these machine identities. This leaves countless gaps for attackers, who increasingly rely on logging in with stolen credentials rather than hacking their way in.
"Cloud is the top cybersecurity threat organizations feel least prepared to manage." - PwC
The consequences of these vulnerabilities are severe. In June 2024, Snowflake, a cloud storage provider, was breached due to infostealer malware that compromised login credentials. This attack affected 165 customers and led to the theft of data from 560 million Ticketmaster customers, including names, addresses, and partial credit card details. Later that year, in December, PowerSchool - a cloud-based software solution - suffered a breach exposing sensitive information for 62 million students and 10 million teachers across 6,000 K-12 schools in the U.S. and Canada.
Relevance to Emerging Threats and Trends
Cloud vulnerabilities are evolving, and new trends are adding complexity to the cybersecurity landscape. One growing concern is the presence of vulnerable AI packages. 62% of organizations have at least one vulnerable AI package in their cloud environment, opening doors to potential attacks through remote code execution flaws.
Edge computing adds another layer of risk. As operational technology (OT) merges with IT and cloud systems, critical sectors like utilities and manufacturing face expanded attack surfaces. For instance, 76% of organizations have at least one public-facing asset that enables lateral movement, meaning a single compromised edge device can provide attackers with access to internal networks.
The situation is further highlighted by high-profile incidents. In 2025, the ShinyHunters hacking group created an extortion website, threatening to release nearly one billion records stolen from companies using Salesforce cloud databases. Victims included major names like Allianz Life, Google, Qantas, and TransUnion. That same year, Google uncovered a hacking campaign targeting Oracle's business products, impacting over 100 companies and resulting in the theft of vast amounts of customer data.
Adding to the challenge is the rise of unstructured data - text, images, videos - driven by GenAI adoption. Traditional database security measures struggle to keep up with the sheer volume of unstructured data now flowing through cloud environments. This shift demands a new, unified approach to security.
Practicality of Implementation for Businesses
Addressing cloud and edge vulnerabilities requires businesses to adopt integrated, risk-based strategies that focus on prevention and visibility.
- Secure your CI/CD pipelines: Integrate security into your development and runtime processes to catch vulnerabilities before they reach production. This is critical, especially when 38% of organizations expose sensitive data in their databases.
- Use attack path analysis: Focus on breaking critical vulnerability chains rather than chasing minor issues. With over one-third of organizations facing risks that enable more than 100 attack paths to high-value assets, prioritization is key.
- Strengthen machine identity management: Create a coordinated strategy to manage machine identities and access. With 78% of organizations having at least one unused IAM role for over 90 days, cleaning up unused credentials can significantly reduce the attack surface.
- Segment and monitor edge environments: For industries like manufacturing, where 97% of organizations have at least one neglected public-facing asset, network segmentation and continuous monitoring are essential.
- Adopt AI-specific security measures: Protect both managed and unmanaged AI models, packages, and data. With 50% of the world’s data (100 zettabytes) expected to be stored in the cloud by 2025, securing AI workloads must be a priority.
These steps are essential to navigating the increasingly complex threat landscape of cloud and edge computing. As the volume of data and the sophistication of attacks grow, proactive security measures will determine how well businesses can protect their assets.
8. Talent Shortages Push Companies to Outsource Security
Impact on Cybersecurity Practices
The global cybersecurity workforce gap has hit a staggering 4 million unfilled positions, with over 700,000 vacancies in the United States alone. Hiring for cybersecurity roles now takes 21% longer than other IT positions, and salaries are soaring. Information security analysts earn a median of $124,910, while senior roles like Chief Information Security Officers (CISOs) often exceed $200,000 annually. These costs make building in-house teams a steep challenge for many companies, forcing them to rethink their strategies.
The shortage of talent is more than just a hiring issue - it’s a risk multiplier. Currently, 87% of organizations worldwide face or expect cybersecurity skill shortages. Add to that the burnout among Security and Risk Management (SRM) leaders, and the need for external expertise becomes even more pressing. Alex Michaels, Senior Principal Analyst at Gartner, emphasizes:
"Cybersecurity burnout and its organizational impact must be recognized and addressed to ensure cybersecurity program effectiveness".
With internal teams stretched thin, many companies are turning to managed services as a way to bridge the gap. These services provide the expertise and scalability that businesses can’t develop quickly enough on their own. This shift is critical as the shortage of skilled professionals exacerbates the challenges posed by increasingly sophisticated cyber threats.
Relevance to Emerging Threats and Trends
The rise of advanced threats, particularly those powered by artificial intelligence, highlights the limits of internal teams. Cybercriminals are using generative AI to launch more sophisticated attacks, while ransomware has evolved into double and triple extortion schemes. Deepfake technology has also become a tool for high-stakes fraud. For instance, in early 2024, a finance employee at a global company was duped into transferring $25 million after participating in a video call where every participant, including the CFO, was an AI-generated deepfake.
These challenges are compounded by growing regulatory demands and increasingly complex threat landscapes. To address these issues, organizations are adopting "SOC 2.0" models, which leverage AI and intelligent agents to handle routine alerts. This frees up human specialists to focus on proactive threat hunting. In fact, 53% of organizations are prioritizing AI and machine learning tools to close internal capability gaps. Morgan Adamski, Principal at PwC US, explains:
"Specialized managed services are also becoming strategic accelerators to provide expertise and scale".
Practicality of Implementation for Businesses
Faced with these pressures, many companies are turning to managed security services to fill critical gaps. The financial benefits are clear: organizations with an incident response team in place save an average of $2.66 million per breach, compared to the $9.48 million average cost of a data breach in the U.S..
To implement this effectively, businesses should start by identifying specific skill gaps, whether in areas like cloud architecture, automation, deepfake detection, or compliance management. Partnering with external providers brings not only proactive threat management but also the regulatory expertise needed to navigate standards like SOC 2, ISO 27001, GDPR, or HIPAA. Look for providers offering 24/7 Managed Detection and Response (MDR) services that seamlessly integrate with your compliance protocols. The ideal partner acts as an extension of your team, delivering both strategic guidance and hands-on support.
How 2025 Trends Will Change in 2026
As we move from 2025 into 2026, the evolution of cybersecurity is set to pick up speed, especially with the rise of autonomous cybersecurity systems. While 2025 was marked by AI tools assisting human analysts, 2026 will usher in AI-native operations where autonomous AI agents can independently analyze, reason, and act. This shift will redefine the dynamics of cybersecurity, transitioning from human-led strategies to machine-speed automation.
Identity: The New Frontline
The battle for cybersecurity is increasingly being fought over identity. Attackers are now exploiting legitimate accounts rather than trying to breach firewalls. This trend will escalate in 2026 with the emergence of AI-generated "CEO doppelgängers" and the growing dominance of machine identities, which already outnumber human identities by a staggering 82-to-1 ratio. Morgan Adamski, Principal at PwC US, emphasizes this shift:
"Adversaries increasingly 'log in' rather than 'break in,' meaning they exploit legitimate accounts and authentication processes to gain access."
This shift in focus from breaking through defenses to exploiting identity opens the door to new threats. One of the most pressing challenges for 2026 will be data poisoning. Instead of just stealing data, attackers will corrupt training datasets, embedding backdoors into AI models. This requires organizations to protect not only structured databases but also unstructured data like text, images, and videos used in large language model (LLM) training and inference.
Regulatory Changes: From Prevention to Resilience
Regulators are also adapting to the rapidly changing landscape. By 2026, the emphasis will shift from prevention-focused mandates to resilience frameworks. New standards will include AI-specific governance requirements and post-quantum cryptographic protocols. Companies leveraging generative AI alongside integrated platform-based security programs could see 40% fewer employee-driven incidents by 2026.
Key Transformations: 2025 vs. 2026
| 2025 Cybersecurity Focus | 2026 Evolution |
|---|---|
| AI tools assisting human analysts | Autonomous AI agents operating independently |
| Phishing and ransomware attacks | AI-driven identity deception and data poisoning |
| Structured data protection | Securing unstructured data (LLM training sets) |
| Reactive SOC monitoring | SOC 2.0: Intelligent automation and proactive threat hunting |
| Human-centric identity management | Machine-centric IAM (82:1 machine-to-human ratio) |
| Privacy compliance (GDPR/CCPA) | AI-specific governance and transparency standards |
| Periodic vendor assessments | Continuous monitoring of supply chains |
| Standard encryption protocols | Post-quantum cryptographic standards |
The cybersecurity landscape in 2026 will be shaped by these transformations, fundamentally altering how organizations defend against increasingly sophisticated threats. The focus will no longer be just on preventing breaches but on building systems capable of adapting and responding at machine speed.
Conclusion
Reactive security simply doesn’t cut it anymore. With cybercrime racking up costs of $10.5 trillion annually and the average breach setting companies back $4.44 million, the stakes have never been higher. Organizations need to move beyond a prevention-only mindset and adopt a resilience-driven approach - one that accepts breaches as inevitable and focuses on minimizing their impact.
And the challenges are only intensifying. By 2026, the threat landscape is expected to escalate even further. Machine identities already outnumber human employees by a staggering 82-to-1, and attackers are shifting tactics - opting to "log in" through identity-centric attacks rather than "break in". Add to this the rise of autonomous AI agents, risks like data poisoning, and the looming need for post-quantum cryptography, and it’s clear that waiting is no longer an option. As Morgan Adamski from PwC US aptly puts it:
"The real differentiator? How cohesively you bring [priorities] together. That means having an empowered, skilled workforce and adopting agile strategies."
For many, specialized managed services are becoming the go-to solution. With a global cybersecurity workforce gap of 4.8 million workers, expert partners are stepping in to fill the void. This ties directly into the execution gap discussed earlier. Cycore stands as a prime example, offering hands-on security and compliance management as an embedded, fractional security team. Cycore doesn’t just monitor compliance - it handles the entire process, from rolling out Zero Trust measures and managing machine identities to conducting vendor assessments and preparing for post-quantum cryptography. Their approach allows your team to focus on innovation and growth while they tackle the heavy lifting.
Looking ahead, companies that act now will be best positioned for success. By streamlining their security tools (with enterprises currently juggling an average of 45 different cybersecurity tools), protecting unstructured data for GenAI applications, and implementing AI-specific governance frameworks, businesses can stay ahead of the curve. In fact, those combining GenAI with integrated security programs are projected to see 40% fewer employee-driven incidents by 2026.
Don’t let compliance and security challenges slow you down. With Cycore, you gain audit-ready compliance, strategic security guidance, and continuous risk management - all for a fixed monthly fee. This means you can stay ahead of evolving threats without the overhead of building an in-house team. The future of cybersecurity demands agility and expertise. Start building resilience today.
FAQs
How is AI changing the effectiveness of cybersecurity strategies?
AI is reshaping the world of cybersecurity, offering powerful tools to bolster defenses and counteract threats. On the defensive side, AI helps security teams act faster by detecting threats in real time, automating responses to incidents, and safeguarding unstructured data such as text, images, and videos. With AI-powered systems, vast data logs can be analyzed swiftly to spot unusual patterns and predict potential risks, giving organizations a critical edge against ever-evolving cyber threats.
But here's the catch - cybercriminals are also tapping into AI to launch more sophisticated and large-scale attacks with minimal effort. This dual-use of AI has created a growing gap between the complexity of threats and many organizations' ability to counter them effectively. To bridge this gap, businesses need to embrace AI-driven solutions for tasks like threat hunting, risk evaluation, and dynamic security controls. At the same time, they must prioritize strong governance, invest in skilled personnel, and stay proactive in managing the rapid advancements in AI technology.
What are the main components of a Zero Trust security model?
Zero Trust is a cybersecurity approach that operates on a simple yet powerful principle: never trust, always verify. Unlike traditional security models that assume everything inside a network is safe, Zero Trust treats every user, device, or system as a potential risk, requiring continuous validation.
Here are its core elements:
- Identity verification: Every user and device must be authenticated and authorized before gaining access, and this process is ongoing, not one-and-done.
- Micro-segmentation: Networks are broken into smaller, controlled zones to restrict access to sensitive systems and data, minimizing the risk of lateral movement.
- Policy enforcement: Access is governed by strict, identity-based rules, ensuring that users and devices only interact with resources they are explicitly allowed to access.
- Encryption: Data is secured both while it’s being transmitted and when it’s stored, protecting it from unauthorized access.
Modern Zero Trust frameworks also integrate automation and real-time monitoring, enabling them to respond dynamically to emerging threats and maintain strong security across increasingly complex, cloud-based environments.
How is the cybersecurity talent shortage impacting strategies?
The shortage of skilled cybersecurity professionals is pushing organizations to rethink how they approach security. With fewer experts available, many businesses are turning to automation, AI-powered threat detection, and managed compliance platforms to simplify processes and cut down on manual tasks.
This gap in talent is also shifting the focus toward protecting the most critical assets and implementing high-priority controls instead of trying to cover every possible vulnerability. To stay ahead, companies are investing in continuous training programs and making strategic hires for specialized roles, ensuring their security strategies remain effective despite the workforce challenges.
By taking these steps, businesses can keep their cybersecurity defenses strong, even as the demand for skilled professionals continues to outpace supply.








































































































